Back to resources
Securing Non-Human Identities: 6 Real-World Use Cases Solved with Britive
December 2024 / 7 min. read /

Non-Human Identities (NHIs): The Unseen Attack Surface In today's cloud-first and automation-driven world, over 90% of identities in the cloud are non-human—such as machine accounts, API keys, OAuth tokens, service accounts, bots, workloads, and scripts. These NHIs are critical for enabling automation, CI/CD pipelines, AI/ML processes, database access, and cloud-native applications.
The Growing Threat:
NHIs are often over-provisioned and static, creating a massive, unseen attack surface. If compromised, NHIs can grant attackers unauthorized access to sensitive systems, databases, or supply chains, leading to data breaches, operational disruptions, and regulatory fines. Their complexity is amplified in multi-cloud and hybrid environments, where managing NHIs at scale becomes challenging.
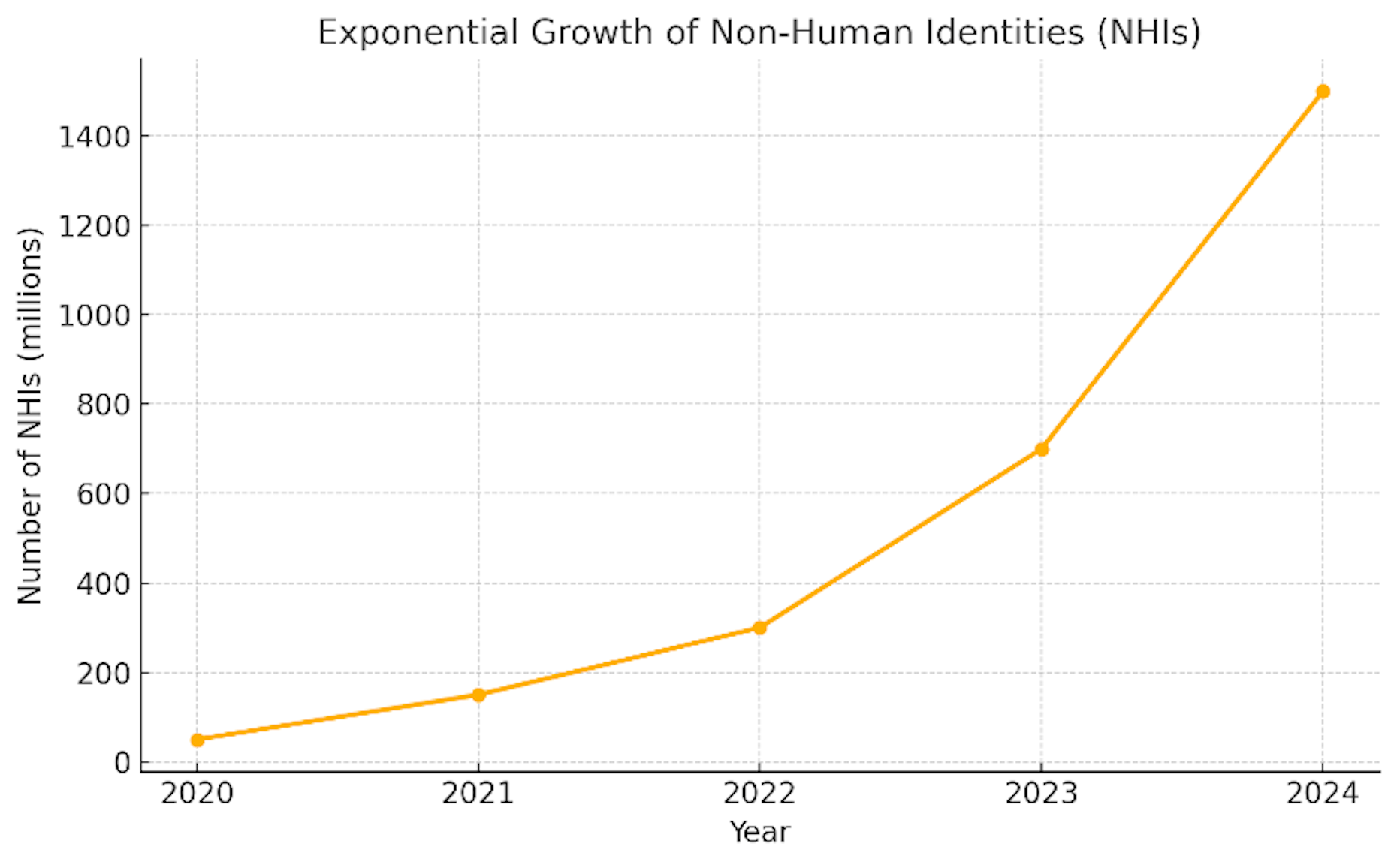
The Cost of Poor NHI Security:
- Data breaches, compliance violations, and financial penalties.
- Disruptions in critical automation, DevOps, and cloud workflows.
- Loss of customer trust and increased cyber insurance premiums.
To highlight the importance of securing NHIs, the following 6 real-world use cases demonstrate how Britive’s unified and dynamic authorization platform mitigates these risks. Each example compares workflows with and without Britive, illustrating the benefits of Just-In-Time (JIT) ephemeral access, task-specific privileges, and robust audit trails.
Did You Know? While organizations implement strong controls for human identities, NHIs—despite being the majority—are often left unchecked. Attackers are increasingly targeting NHIs to gain lateral movement in the cloud and exfiltrate data without being noticed.
The examples below showcase actionable examples where Britive helps secure NHIs to protect sensitive data, ensure compliance, and reduce the risk of breaches.
1. GitHub CI/CD Pipeline Automation
Description: Automates application deployment using GitHub Actions and AWS resources, including databases with sensitive configurations.
Steps:
- Developer pushes code to GitHub.
- Workflow authenticates with an AWS RDS instance using an API key to apply schema changes.
- Updates are deployed to the application servers.
- Application logs are accessed for testing and monitoring.
Without Britive:
- Static API key stored in GitHub secrets.
- API key used to access sensitive AWS resources, including RDS databases.
- Key persists, increasing exposure risk.
- Risk: Non-compliance with DevSecOps best practices can lead to regulatory fines and increased cyber insurance premiums.
With Britive:
- JIT ephemeral API key provisioned dynamically.
- Key scoped to task-specific AWS access.
- Key expires immediately post-deployment, reducing the attack surface.
Benefits:
- Protects sensitive database configurations.
- Ensures compliance with DevSecOps standards.
- Reduces risk of credential misuse, mitigating impact on cyber insurance.
2. RPA Automation for Invoice Processing
Description: RPA bots process invoices by retrieving and validating data from financial databases via an ERP system.
Steps:
- Customer uploads an invoice.
- RPA bot retrieves invoice metadata from an ERP system's sensitive database.
- Financial records, such as payment history, are validated using an API key.
- Invoice is forwarded for approval or flagged for anomalies.
Without Britive:
- Static credentials stored in bot configuration files.
- Credentials grant broad access to the ERP database, exposing sensitive financial data.
- Persistent credentials increase risk of insider threats.
- Risk: Breach of sensitive financial data could violate SOX compliance and increase cyber insurance costs.
With Britive:
- Ephemeral API keys provisioned dynamically at runtime.
- Scoped keys provide read-only access to specific database tables.
- Credentials expire immediately after the task concludes.
Benefits:
- Secures financial databases by enforcing least privilege.
- Meets SOX requirements for sensitive data handling.
- Reduces cyber insurance premiums by mitigating insider threat risks.
3. Loan Approval Workflow in Azure with Fraud Detection
Description: Automates loan approval by retrieving sensitive financial records and integrating with fraud detection services.
Steps:
- Customer submits a loan application.
- Azure Logic App retrieves applicant’s financial history from Azure SQL Database.
- Logic App integrates with third-party APIs to fetch credit scores and run fraud checks.
- Loan eligibility is evaluated, and a decision is communicated to the customer.
Without Britive:
- Static client secrets stored in Logic App configurations.
- Secrets grant access to sensitive Azure SQL Database and third-party APIs.
- Persistent credentials are susceptible to theft, compromising financial records.
- Risk: Credential misuse could lead to GDPR violations and increase regulatory penalties.
With Britive:
- JIT service principal tokens provisioned dynamically.
- Tokens scoped to access specific tables in Azure SQL Database and APIs.
- Tokens expire immediately after workflow execution ends.
Benefits:
- Protects financial and personal data in databases.
- Ensures GDPR compliance.
- Mitigates regulatory and cyber insurance risks.
4. Securing Insurance Claim Processing Workflow with Britive
Description: Automates claims validation by accessing sensitive customer records and integrating with fraud detection APIs.
Steps:
- Customer submits a claim online.
- Azure Logic App retrieves claim-related documents (e.g., invoices, photos) from Azure Blob Storage.
- Azure Function validates the claim via a fraud detection API, which accesses customer credit data.
- Decision is sent to the customer or insurance adjuster.
Without Britive:
- Static credentials stored in Azure Functions to access Blob Storage and APIs.
- Credentials allow broad access to sensitive customer files and external systems.
- Persistent credentials are a high-value target for attackers.
- Risk: Breach of sensitive data may violate GDPR and result in higher cyber insurance premiums.
With Britive:
- Ephemeral credentials provisioned dynamically.
- Scoped access to specific containers in Blob Storage and fraud detection APIs.
- Credentials expire immediately after the task is completed.
Benefits:
- Protects sensitive customer and claims data.
- Ensures compliance with GDPR and HIPAA.
- Reduces regulatory and insurance-related risks.
5. Securing Healthcare Data Processing Workflow (Azure & AWS) with Britive
Description: Processes patient data by accessing sensitive records in hybrid cloud storage and integrating with APIs for insurance validation.
Steps:
- Patient schedules an appointment via an online portal.
- Azure Logic App retrieves patient records from Azure Blob Storage, including medical history and lab results.
- AWS Lambda accesses patient billing data from an S3 bucket.
- Workflow integrates with external APIs for insurance validation and scheduling.
- Consolidated data is presented to the doctor for the appointment.
Without Britive:
- Static secrets stored in Azure Logic App and AWS Lambda configurations.
- Secrets grant access to Blob Storage, S3, and sensitive APIs.
- Persistent credentials expose medical and billing data to breaches.
- Risk: Non-compliance with HIPAA could result in significant fines and affect cyber insurance coverage.
With Britive:
- JIT ephemeral tokens provisioned for Logic App and Lambda.
- Tokens scoped to specific containers in Blob Storage and S3 buckets.
- Tokens expire immediately post-task, ensuring minimal exposure.
Benefits:
- Protects sensitive healthcare data across Azure and AWS.
- Ensures compliance with HIPAA and GDPR.
- Mitigates regulatory penalties and lowers insurance premiums.
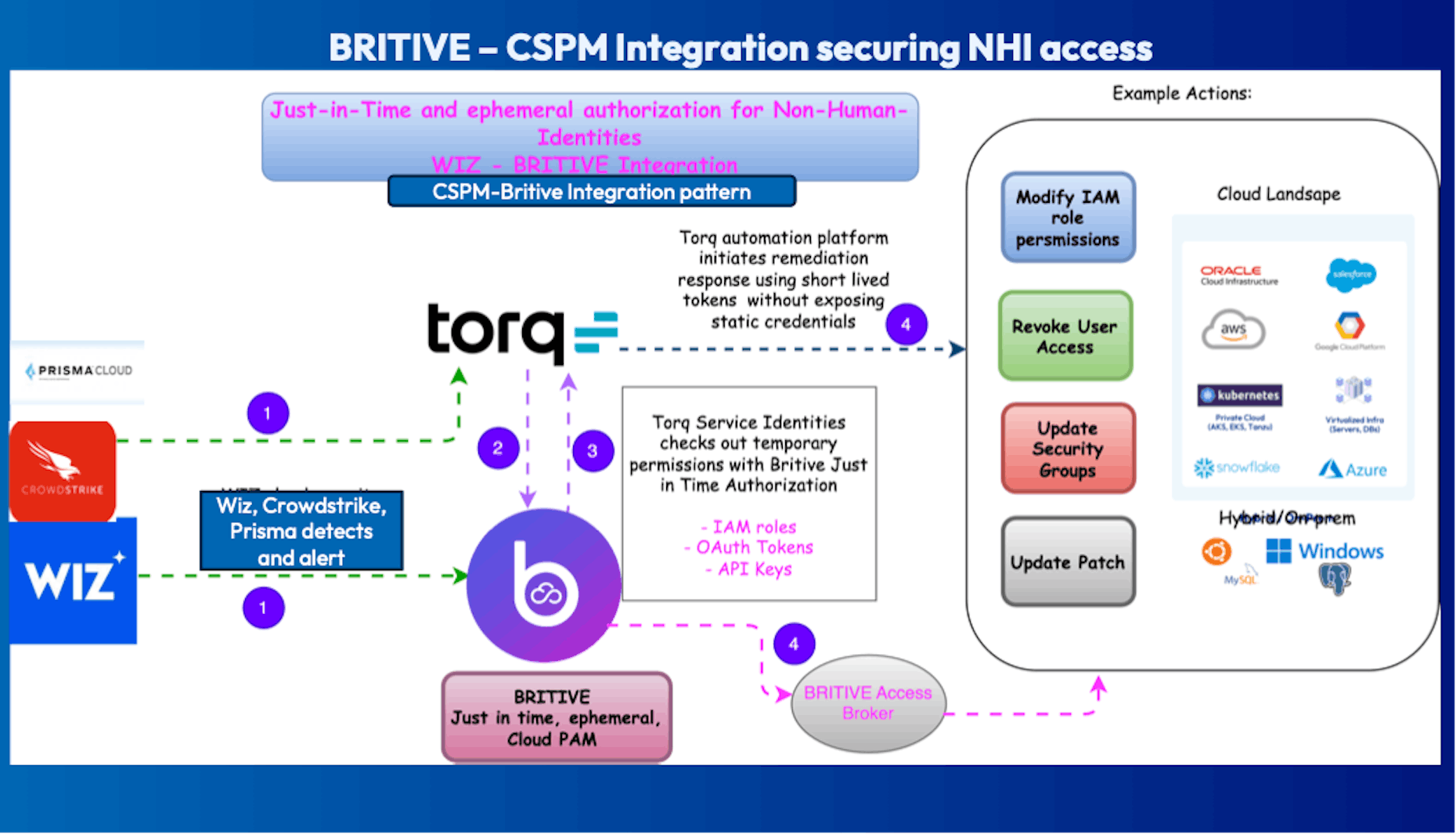
6. Automated Threat Detection and Response for Data Storage with CSPM and Britive Integration
Description: Automates the detection and remediation of misconfigured cloud storage buckets (e.g., Amazon S3) using CSPM, SOAR, and Britive integration, minimizing the risk of data leakage.
Steps:
- Detection: A CSPM tool (e.g., Wiz, CrowdStrike, Prisma) identifies a misconfigured, publicly accessible S3 bucket.
- Alert Generation: The CSPM tool generates an alert for the misconfiguration.
- Automation: A SOAR platform (e.g., Torq) receives the alert and triggers a remediation workflow.
- Access Management: Britive provides JIT, ephemeral access to a non-human identity (e.g., automation script) for remediation.
- Remediation: The misconfiguration is corrected, securing the S3 bucket.
- Documentation: The entire workflow is logged and sent to a SIEM for compliance and audit purposes.
Without Britive:
- Static IAM credentials or access keys are stored in the SOAR tool.
- Credentials provide broad, persistent access to all S3 buckets.
- Increased risk of misuse or exposure of static keys.
- Manual intervention needed to revoke access, delaying remediation.
With Britive:
- Britive dynamically provisions JIT ephemeral credentials scoped to the specific misconfigured S3 bucket.
- Credentials are limited to the task of remediation and expire immediately after use.
- Access logs are generated and sent to the SIEM for audit and compliance.
- Workflow is automated and secure, eliminating static credential risks.
Benefits:
- Prevents unauthorized access by eliminating static IAM credentials.
- Ensures rapid, secure remediation of misconfigurations.
- Meets compliance standards by maintaining detailed audit trails.
- Reduces operational risks associated with public cloud misconfigurations.
- Supports Zero Trust principles with dynamic, task-specific access.
Ready to learn more about how Britive can secure NHIs across your environment? Schedule some time to talk with our team to see how the multi-cloud PAM platform works firsthand.