


Access Broker
Extend Cloud-Native PAM Capabilities to Hybrid and On-Prem Environments

Secure Access Management for Every Environment
Modern enterprises operate cohesively across complex multi-cloud and hybrid on-premises environments, but access management remains fragmented.
Different policies, identity systems, and security controls implemented with a fragmented and siloed approach in tools and strategy result in security blind spots, risks due to persistent, high-privilege accounts, limited flexibility, and complex deployments.
Britive’s Access Broker extends cloud-native just-in-time (JIT) permissions to cloud-first, hybrid on-prem, and private cloud environments to extend frictionless, secure access management everywhere.
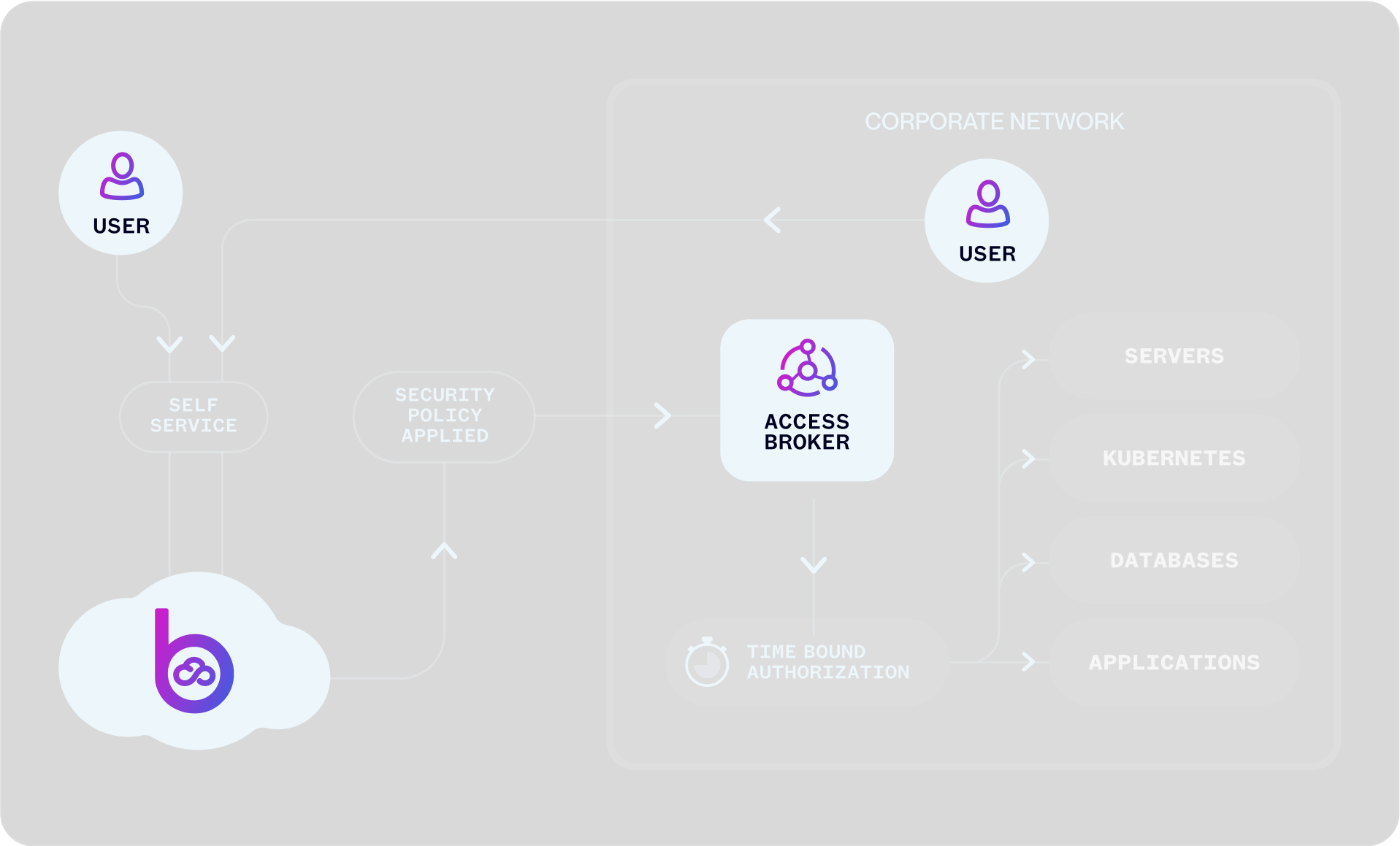
AccessBroker
Cloud PAM that Works Anywhere
Britive extends the power of dynamic, ephemeral JIT permissions to resources beyond the public cloud to secure servers, databases, internal applications, and private network resources without credentials or standing privileges. Privileged access management is unified and simplified through a single, easy-to-use platform across the entire environment.
[ 001 ]
Unified Dynamic JIT Access Management
Extend Britive’s JIT ephemeral permissions model to hybrid, private cloud, and on-prem resources to eliminate standing privileges for both human and non-human identities. Ensure secure, temporary access to critical infrastructure and applications no matter where they reside.
[ 002 ]
Universal Platform for Resource Access Management
Manage privileged access for all identities across public cloud, private cloud and hybrid environments, on-prem servers, databases, VMs, and applications through a single platform. Integrate seamlessly with all your existing tools.
[ 003 ]
Support Cloud Migration & On-Prem Resources
Secure legacy applications and infrastructure awaiting cloud migration. Ensure consistent access policies across hybrid and cloud-native environments and streamline migration efforts without security gaps.
[ 004 ]
Eliminate Standing Privileges & Strengthen Security
Quickly apply Britive’s patented ephemeral JIT permissions to on-prem resources and eliminate static credentials and overprivileged accounts. Achieve zero standing privileges (ZSP) across complex hybrid infrastructures according to any requirements.
Access Broker: Secure Hybrid Access Without Complexity
REQUEST A DEMOREQUEST A DEMO
Adaptable JIT Implementation for Security without Disruption
Our policy-driven approach to privilege management gives users the ultimate flexibility while providing centralized visibility and control. Seamless, ephemeral access can be configured as needed for any environment with no VPNs, firewall changes, or additional infrastructure.
Comprehensive, Centralized Access Management
Unify access to virtually any resource type, regardless of where it’s located. Integrate with cloud services (SaaS, DaaS, PaaS), cloud infrastructure (IaaS, Kubernetes), servers (physical, VMs) databases, applications, and more. Monitor and manage privileged access through a single tool to reduce operational efficiency and address blind spots from fragmented approaches.
Reduce Privilege Risk in Any Environment
Eliminate standing and overprivileged permissions with the same ephemeral access technology pioneered for cloud infrastructure. Reduce risk in on-prem and private infrastructure by extending least privileged access and zero standing permissions.
Future-Proof Access Security
Secure access to on-prem and cloud environments during migrations or architecture changes. Maintain a unified access strategy across the entire environment and adapt rapidly to new and upcoming tools and requirements.
REQUEST A DEMOREQUEST A DEMO

