


Back to resources
Modern Identity Security Practices for PCI DSS 4.0 Compliance
January 2025 / 4 min. read /

The Payment Card Industry (PCI) Data Security Standards (DSS) are international security guidelines established to safeguard cardholder information and prevent credit card fraud. The standard has undergone multiple revisions over the decades of its existence, each designed to further enhance security and keep pace with evolving technology considerations.
PCI DSS v4.0 is the latest major iteration, supplanting v3.2.1. It introduces significant updates to ensure that organizations continue to meet the payment industry's evolving security needs and to address increasingly sophisticated cyberattacks.
As of March 2024, PCI DSS v4.0 is the active version. It is essential to the understand the requirements of v4.0 and ensure any necessary adaptations or changes from previous versions are in place.
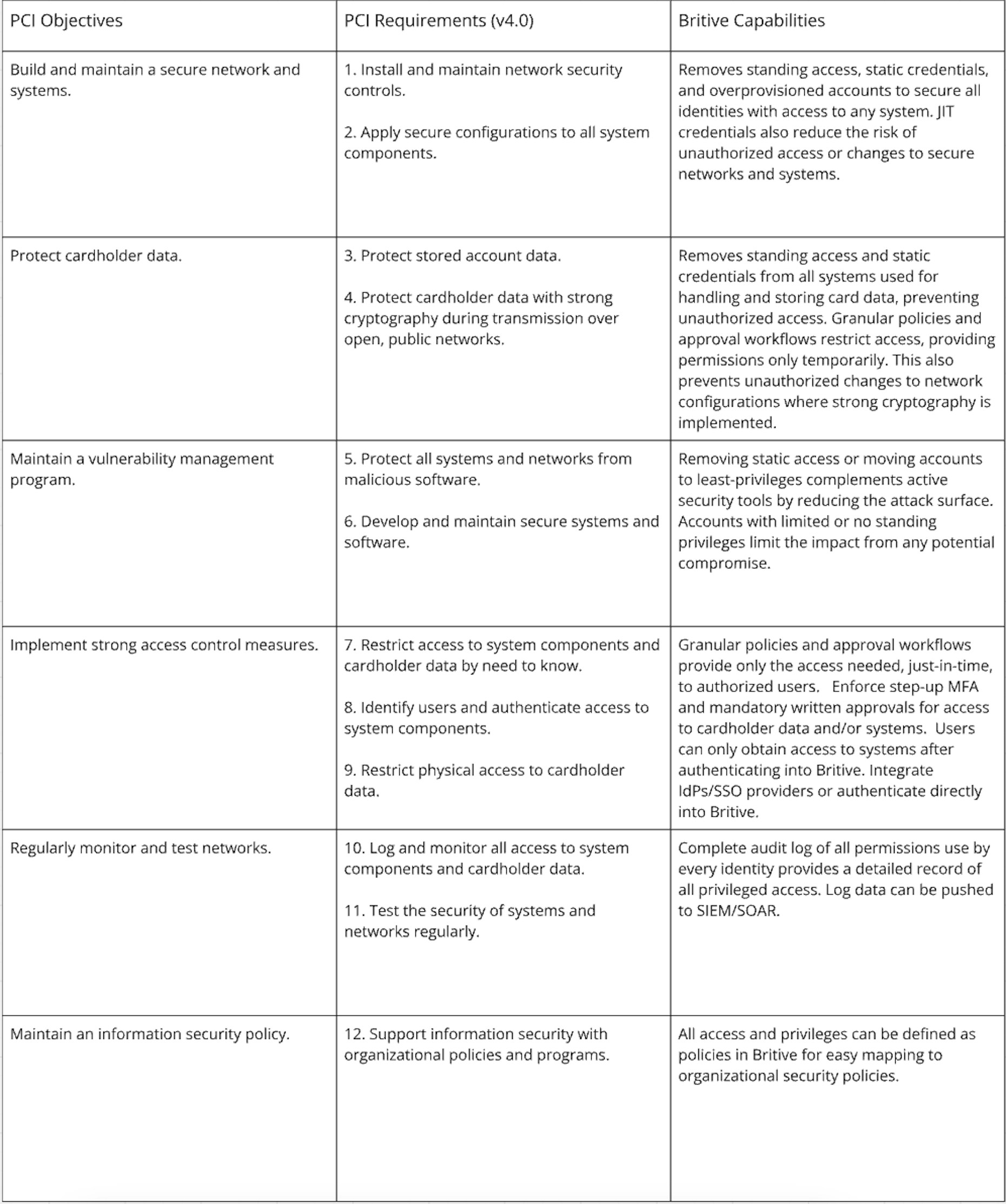
PCI DSS v4.0 maintains the 12 core requirements for handling cardholder data and maintaining a secure network, which are organized into six primary objectives. These objectives outline what you will achieve with PCI DSS compliance, while the 12 requirements provide detailed guidance on how to meet those objectives.
As you transition to PCI DSS v4.0, reviewing the changes and enhancements in this version will help ensure that your organization remains compliant with the latest security standards.
Britive’s dynamic, just-in-time (JIT) privileges, granular access policies and approval workflows, and robust visibility and audit logs can be a foundational piece of a PCI DSS v4.0-compliant security program. Below are key capabilities of the Britive platform mapped against the 12 core requirements.
Suggested Steps for PCI DSS Compliance
Financial organizations and others that handle payment card information can take the following steps to align their access management strategies with PCI DSS v4.0:
- Inventory All Privileged Access: Conduct a thorough assessment of human and non-human identities across the entire environments. Identify all privileged accounts, roles, and entitlements for a baseline understanding of all the identities and what they have access to.
- Implement Temporary, Time-Bound Access: Transition from standing privileges to just-in-time (JIT) access. Enforcing time-bound access for both human and non-human identities ensures that access doesn't exist for longer than required, reducing the risk of potential targeting and exploitation. By making all access temporary, organizations can achieve zero standing privileges (ZSP), reducing the potential for access creep and the need to review and attest to the access currently associated with each account.
- Enforce Well-Defined Access Policies: Establish granular access policies that align with the needs of the user or automation as well as regulatory requirements. Additional contextual factors such as the user's role, device, and other information can be used to ensure that the access granted is appropriate to their needs, ensuring adherence to the principle of least privilege.
- Automate Compliance Auditing: Leverage well-integrated automation tools where possible to continuously track, log, and report access events. This helps ensure compliance readiness and streamlines audit processes by eliminating manual, time-consuming periodic access reviews.
- Continuously Monitor Access: Utilize advanced monitoring solutions integrated with other visibility and alerting tools to detect and respond to suspicious activities in real-time. Proactive alerting mechanisms to mitigate potential threats before they escalate.

