


Back to resources
NIST CSF 2.0 and Least Privilege: Bridging Gaps in Identity Security
January 2025 / 11 min. read /

The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) has long been a cornerstone for organizations aiming to bolster their cybersecurity posture. With the release of NIST CSF 2.0 in early 2024, the framework expands its focus, offering updated guidelines to address today’s evolving threat landscape. It is the result of a multi-year collaboration between the private sector, the US public sector and governments around the world, and academic researchers.
There is an important consideration to understand when evaluating the CSF as part of your security and identity practices. The CSF does not offer prescriptive guidance for how outcomes should be achieved. The framework does provide links to resources that provide additional guidance on practices and controls that can be used to achieve its outcomes, although there are many options for each objective. However, in areas where the CSF has coverage gaps or could go even further, you must look elsewhere for both guidance and solutions.
While the new version brings significant benefits, it’s essential to evaluate both its advantages and potential drawbacks to understand its impact on your organization’s security strategy. As you will see, there are multiple steps in the direction of improved identity security posture, yet gaps still remain—especially when it comes to cloud systems. We will be looking at the Cloud Security Alliance’s (CSA) Cloud Controls Matrix (CCM) v4 to highlight some of these gaps and recommendations for going beyond NIST CSF 2.0.
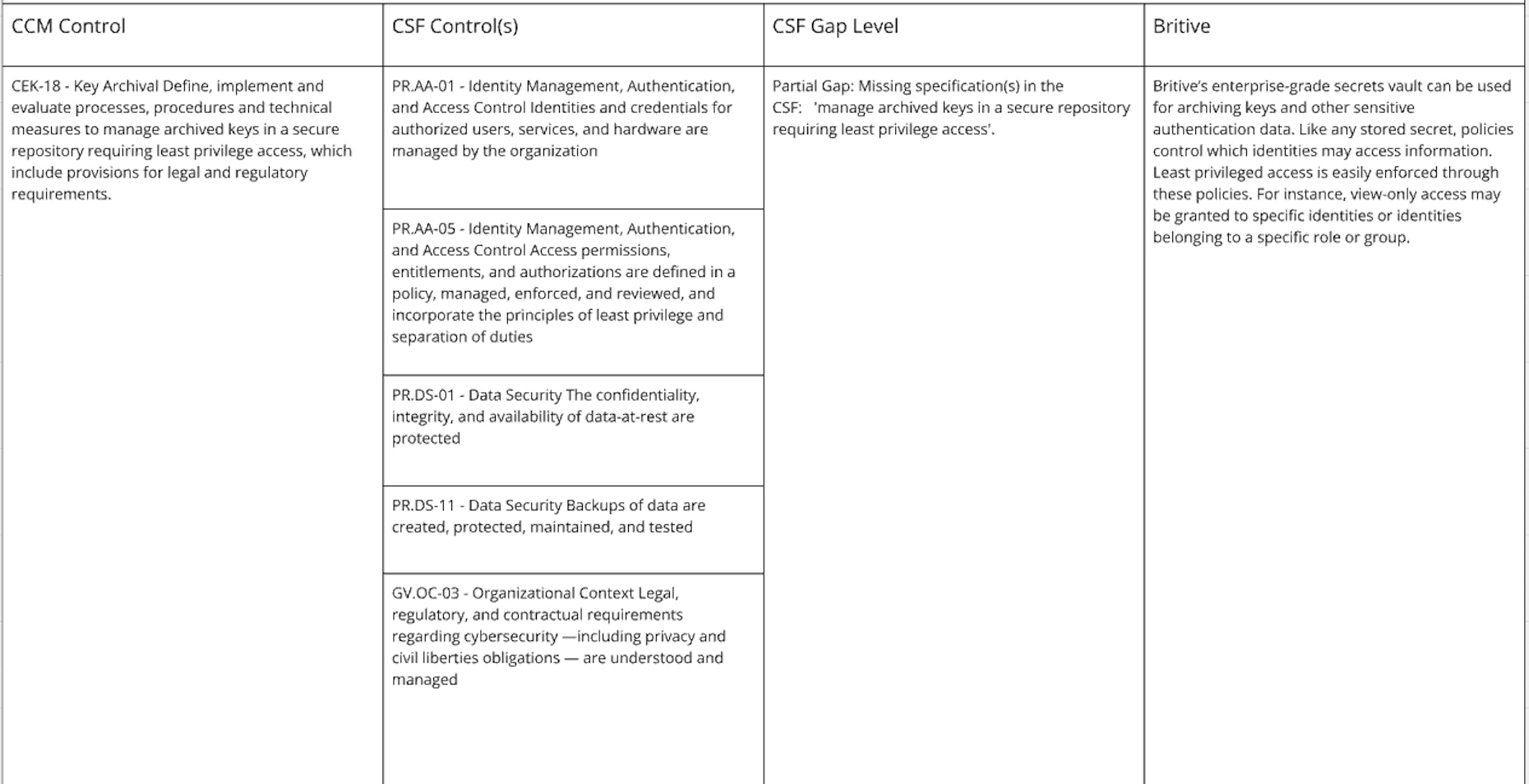
Cryptography, Encryption & Key Management
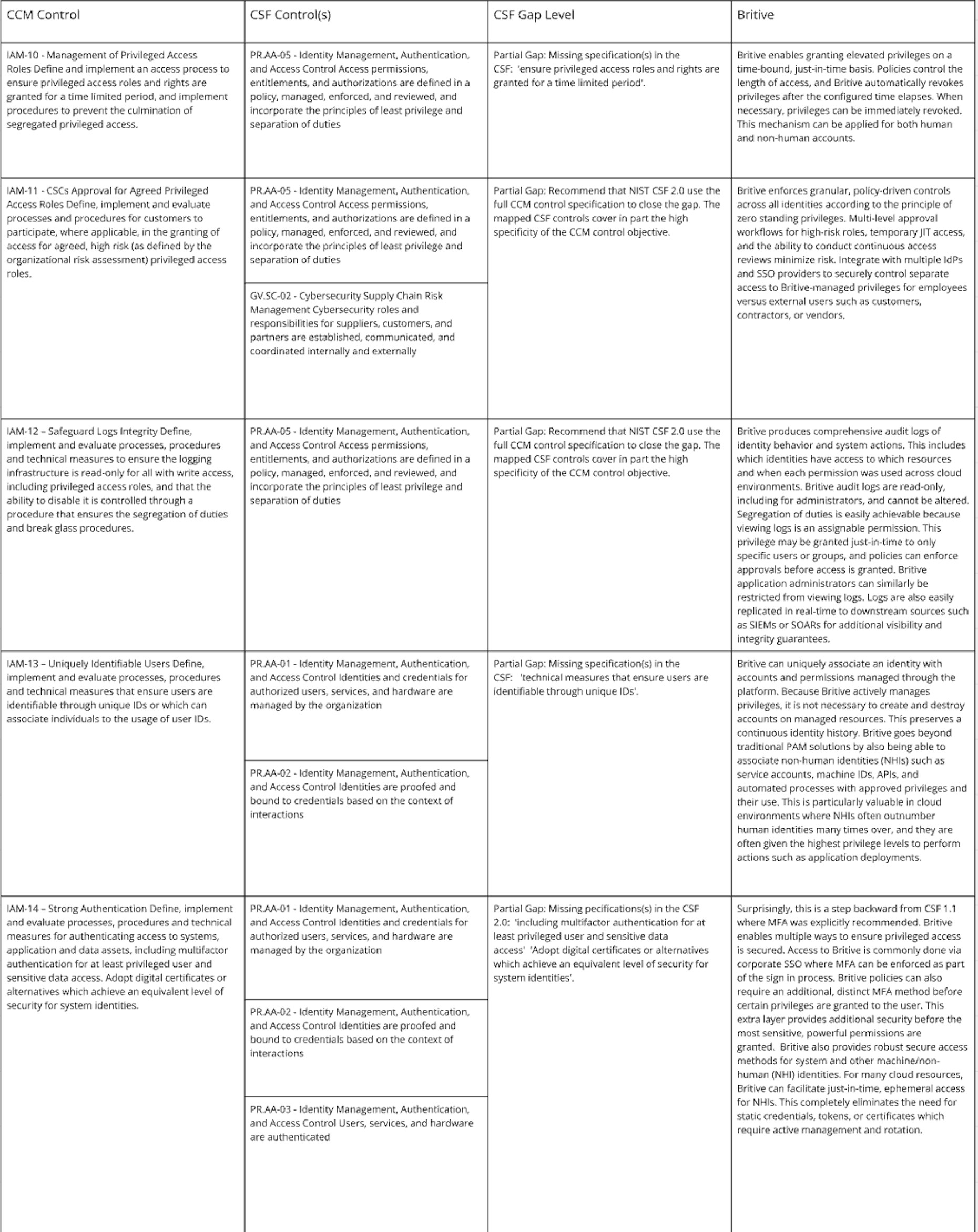
Identity & Access Management
Logging & Monitoring
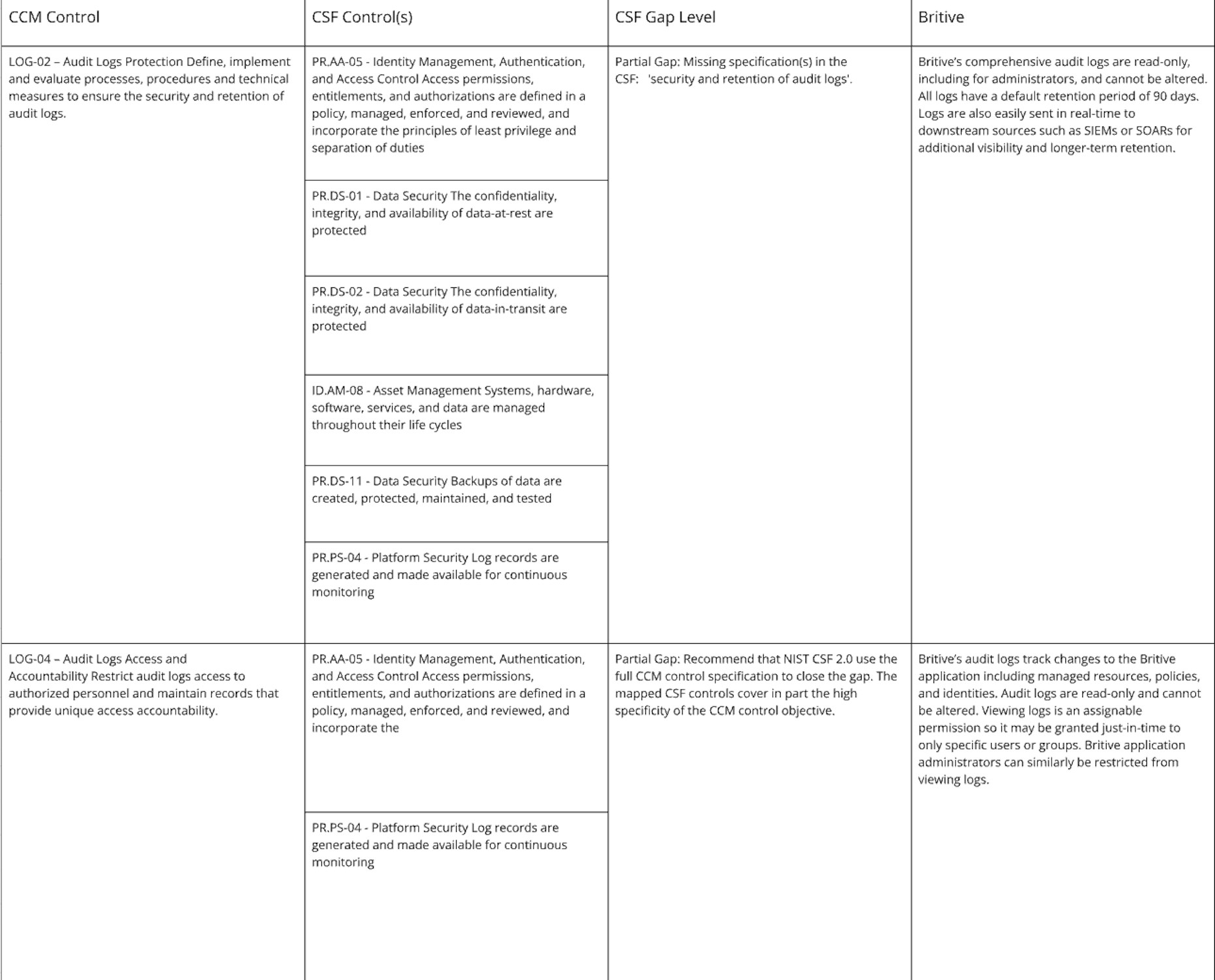
Both CSF and CCM frameworks have far more controls than listed above. These are only the identity- and authorization-focused areas concerned with implementing systems or processes where NIST CSF 2.0 could go even further in its security recommendations such as by adopting the extra controls in CCM v4.
The good news for identity-focused security practitioners is the are many areas where coverage is aligned between the two frameworks. This should make evaluating the right security tools and practices that have the broadest coverage an easier task. And as with any such frameworks that lack prescriptive guidance, use your best judgement and don’t be afraid to augment a singular framework with additional controls.
Want to learn more about how Britive can help you meet requirements for NIST CSF 2.0, CSA CCM v4 or other cybersecurity frameworks? Schedule time to chat with a member of the team or get a personalized demo.


