
ISO/IEC 27001 and ISO/IEC 27002 are internationally recognized standards designed to help organizations secure their information assets and manage risks associated with data security. They are part of the broader ISO/IEC 27000 family of standards, which provides a comprehensive framework for managing and protecting sensitive information.
ISO/IEC 27001 is the main standard that specifies the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). The ISMS is a systematic approach to securing sensitive information so that it remains secure. It includes policies, processes, and controls that are aligned with an organization’s risk management strategy to protect the confidentiality, integrity, and availability of information. This is critical in safeguarding against identity theft and unauthorized access. ISO 27001 certification demonstrates to stakeholders that an organization meets globally accepted information security standards.
ISO/IEC 27002 is a supplementary standard that provides detailed guidance and best practices for implementing the controls listed in ISO/IEC 27001. While ISO 27001 focuses on the "what" — the requirements of an ISMS — ISO 27002 focuses on the "how" by offering practical advice on the implementation of security controls. It covers various aspects of information security, including access control, cryptography, physical and environmental security, identity and access management, and incident management, helping organizations to choose and apply appropriate controls to manage risks effectively.
The two standards work together to enhance an organization’s security posture. ISO 27001 is used for certification, signaling a commitment to robust information security practices, including the protection of identity data.
ISO 27002 plays a critical role by providing the detailed guidelines needed to implement the controls outlined in ISO 27001, including those related to identity and access management. Pursuing ISO 27001 certification, with the practical guidance from ISO 27002, helps organizations build trust with customers and partners, reduce the risk of data breaches, and ensure compliance with legal and regulatory requirements concerning identity protection.
Focusing on identity aspects is crucial because identity data is often a prime target for cybercriminals. By adhering to both ISO 27001 and ISO 27002, organizations can better secure this sensitive data, effectively mitigating the risk from identity compromises. These standards ensure that access to information is properly managed, monitored, and controlled, providing a comprehensive approach to safeguarding identity-related information.
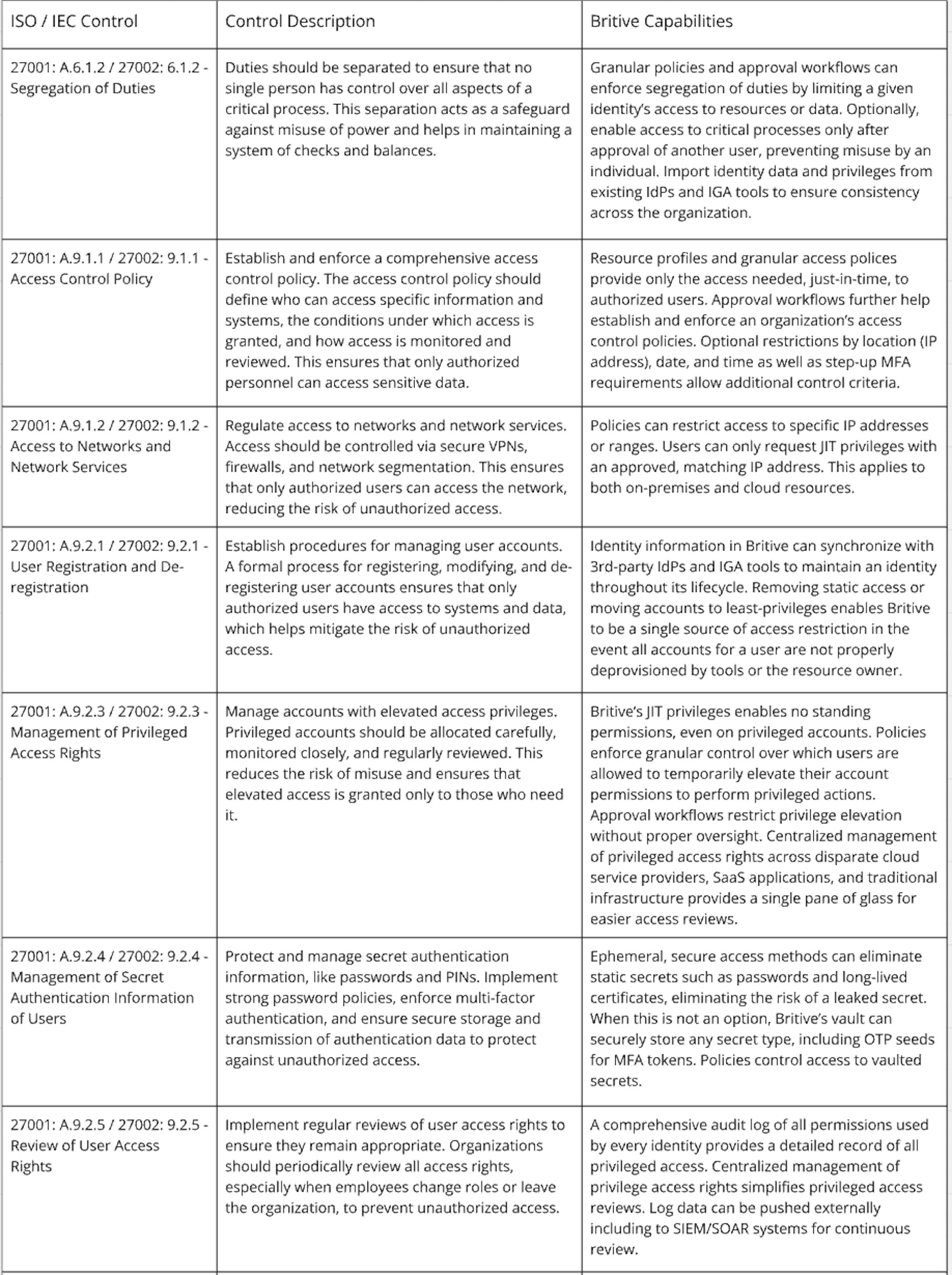
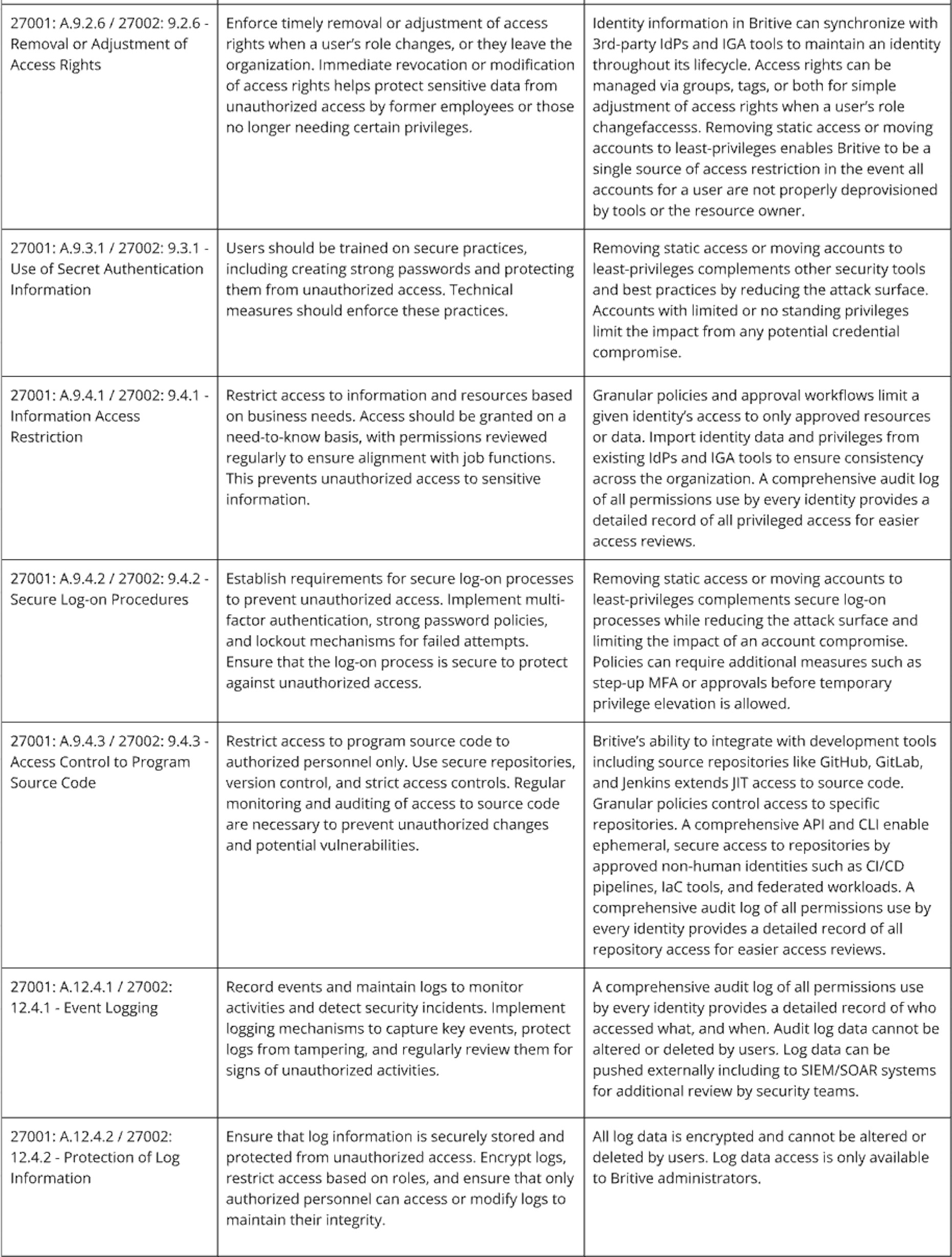
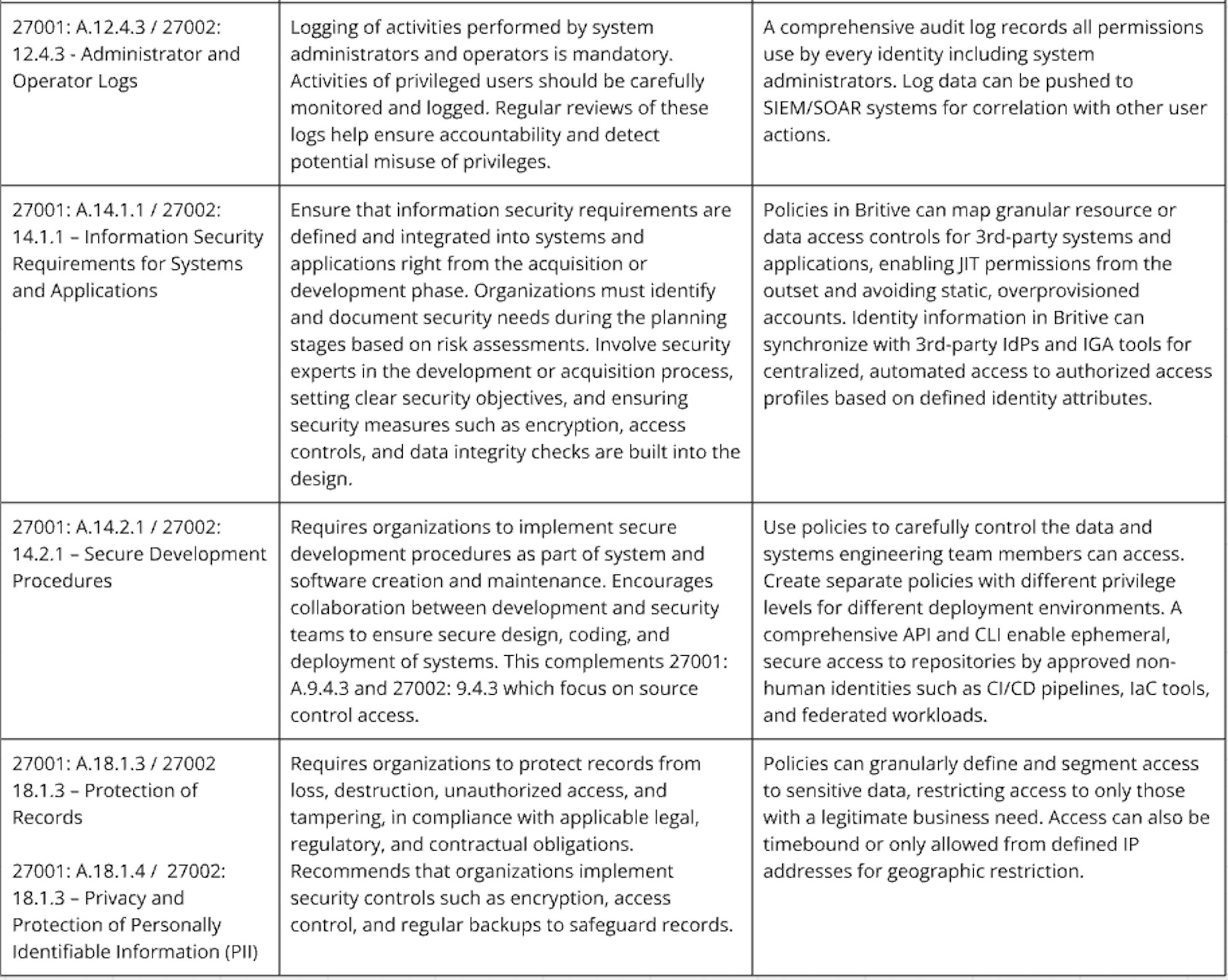
Britive’s dynamic, just-in-time (JIT) privileges, granular access policies, approval workflows, and robust visibility and audit logs can play a crucial role in achieving ISO 27001 certification and implementing ISO 27002 controls. These capabilities support the establishment of a secure and well-managed Information Security Management System (ISMS) by enabling precise access control, effective monitoring, and detailed audit trails. Below are key features of the Britive platform mapped to specific ISO 27001 requirements and ISO 27002 guidelines.
Ready to learn more about how Britive can help your organization meet compliance for ISO / IEC or other regulatory requirements?
Schedule time to chat with a member of the team or get a personalized demo.




