


Back to resources
SOC 2 Compliance: Secure Privileged Access to Data with CPAM
February 2025 / 7 min. read /

SOC 2 (System and Organization Controls 2) is a widely recognized auditing standard developed by the American Institute of Certified Public Accountants (AICPA). It is designed to evaluate and report on the effectiveness of an organization's information security controls related to the five Trust Service Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Unlike various other frameworks that are mandated for certain industries or businesses performing certain activities (HIPPA, PCI, Sarbanes-Oxley), SOC 2 certification is entirely voluntary and can be adopted by any kind of organization. SOC 2 compliance demonstrates a commitment to protecting sensitive information and maintaining robust security practices. It is particularly important for service providers and organizations that handle customer data.
Another key aspect of SOC 2 is it provides a general framework of controls but is not prescriptive in the specifics of how each control is implemented or enforced. This provides flexibility for the organization. Some controls may only require a documented process. For others, a tool is required, but it is up to the business to choose the appropriate solution. SOC 2 is broad enough in scope that it will require multiple solutions in different categories to provide complete coverage. With careful selection, a single tool can fully or partially meet the requirements for many controls.
One of the key aspects of SOC 2 compliance is ensuring that only authorized individuals have access to critical systems and sensitive data. This is where Privileged Access Management (PAM) tools become essential. PAM tools help organizations enforce strict controls over who can access privileged accounts—those with elevated permissions that can potentially affect the entire environment or business. By managing, monitoring, and securing these privileged accounts, a PAM tool reduces the risk of unauthorized access, data breaches, and internal threats, which are critical concerns under the security criterion of SOC 2.
PAM tools are also mission-critical systems for most organizations, controlling access to broad swathes of their systems and infrastructure. Selecting the right solution can offer significant coverage for a SOC 2 audit as the capabilities of modern PAM tools extend beyond just protecting credentials.
Britive can play a key role in helping organizations achieve SOC 2 compliance. It goes beyond simply protecting credentials with a broad set of platform capabilities that cover many key controls. Below are specific sections or criteria within the SOC 2 framework where Britive can help.
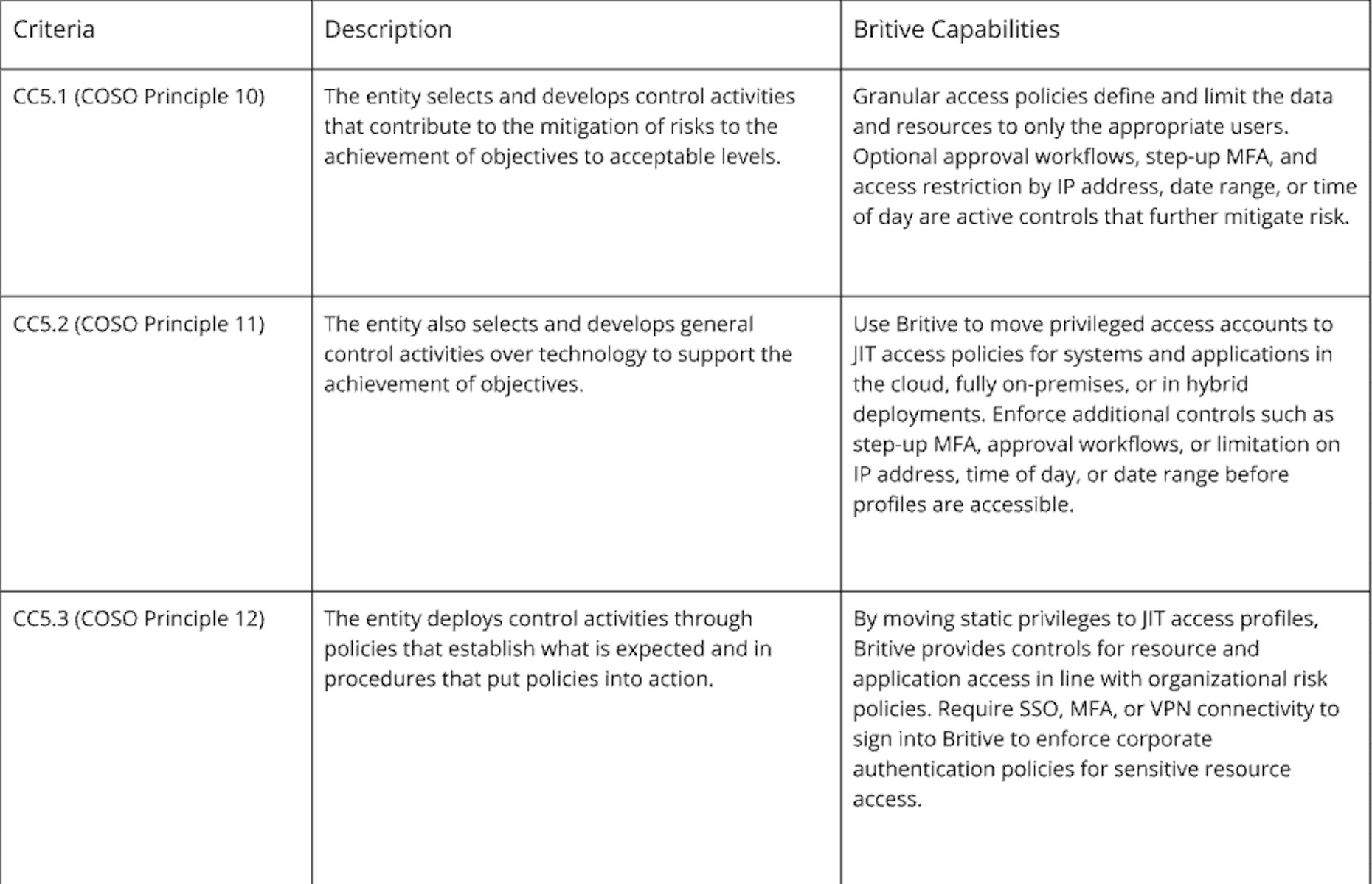
Logical and Physical Access Controls (CC6)
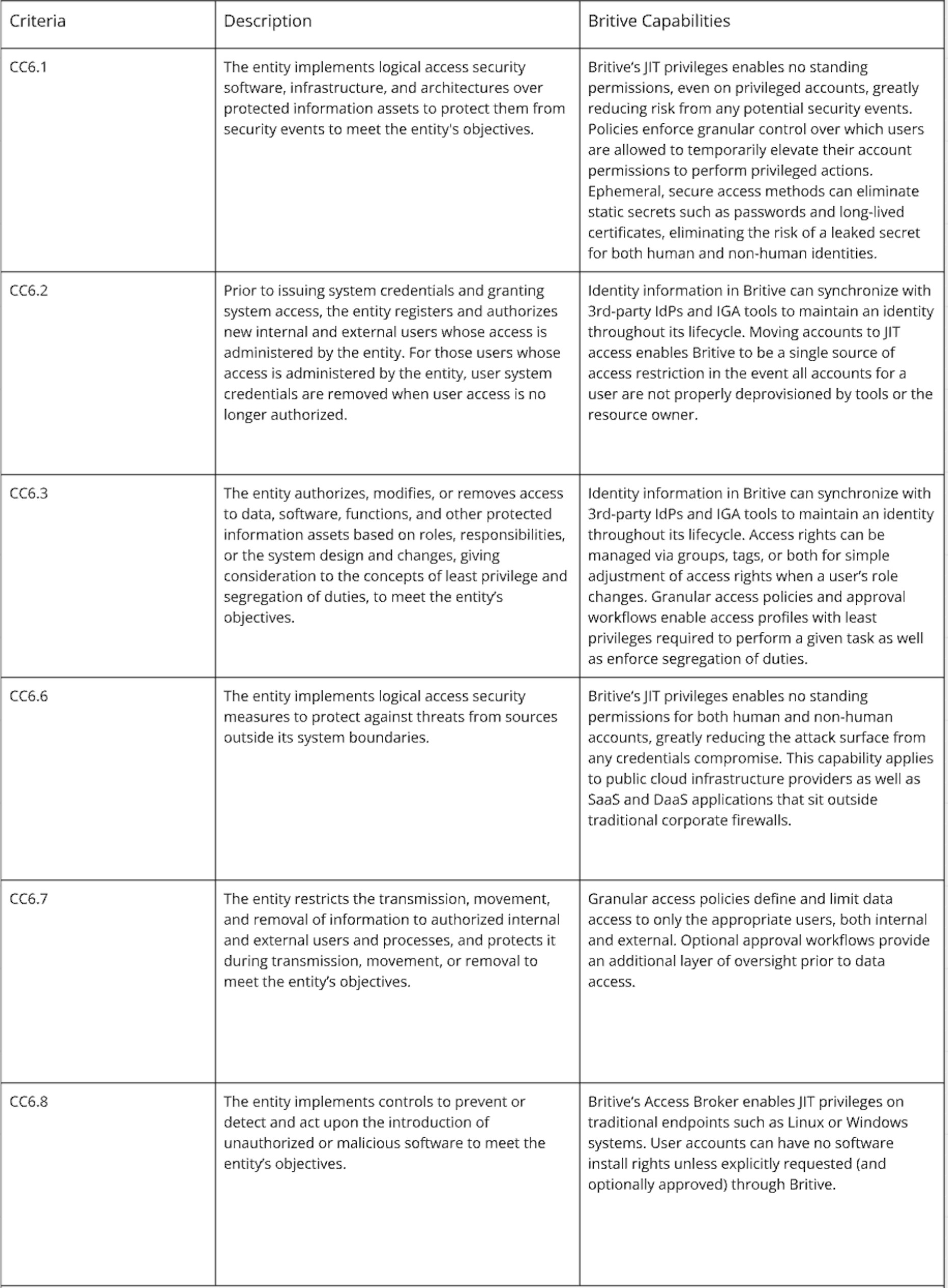
Risk Assessment (CC3)
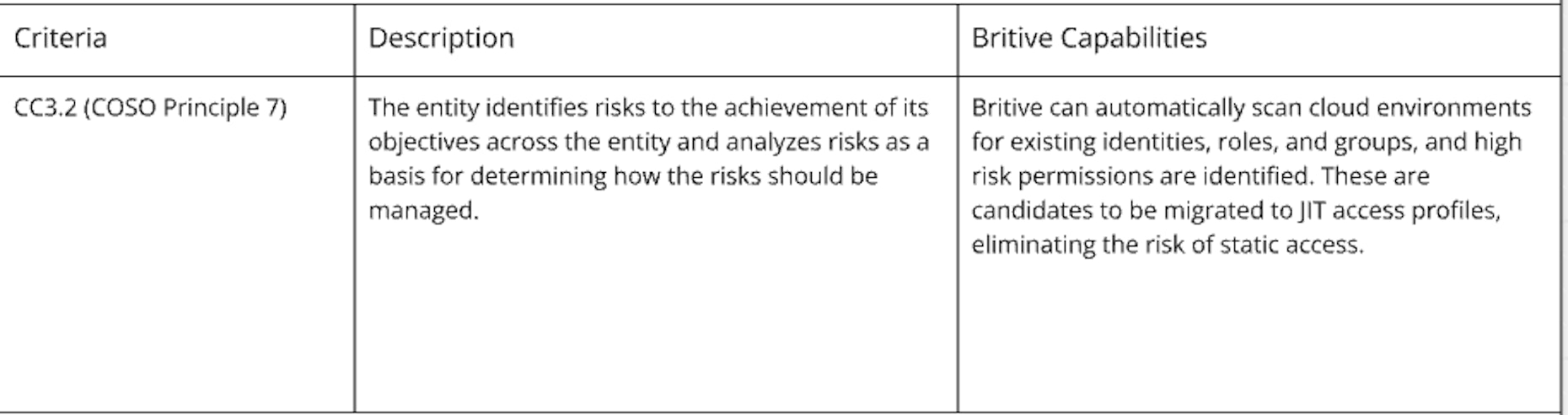
System Operations (CC7)
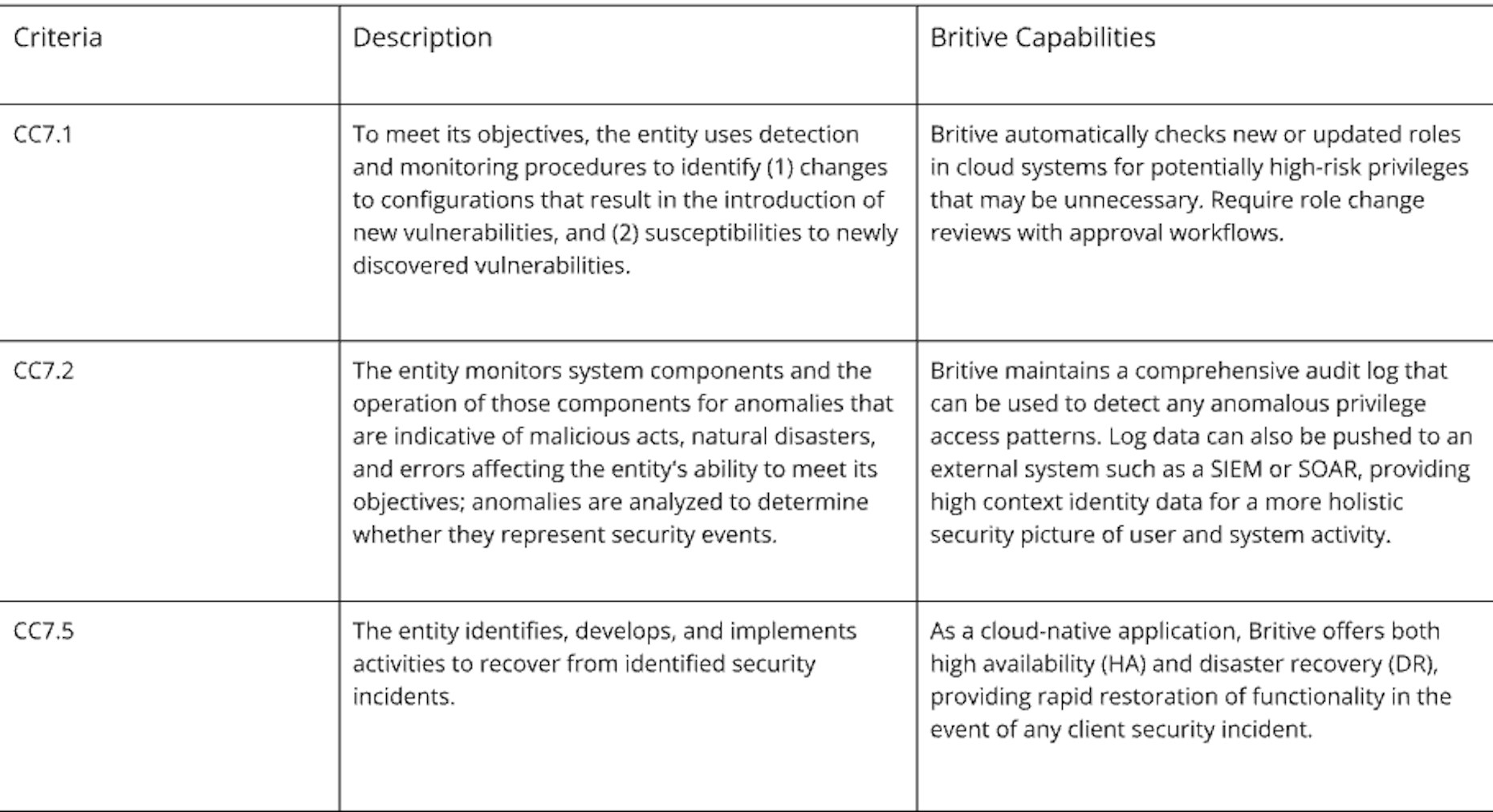
Control Activities (CC5)
Change Management (CC8)
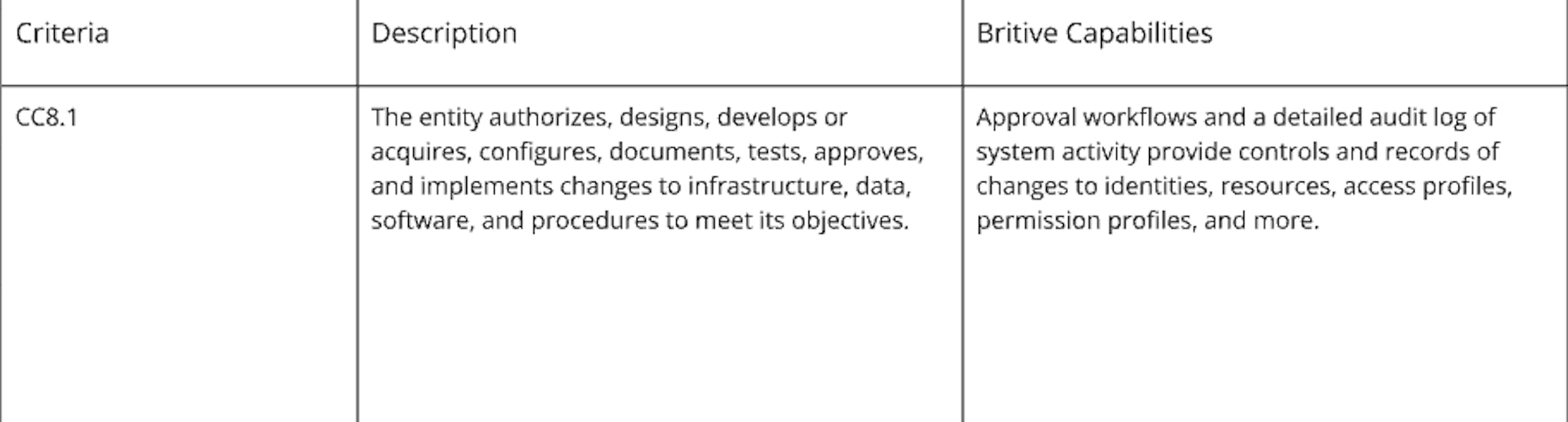
Confidentiality Criteria

Availability Criteria
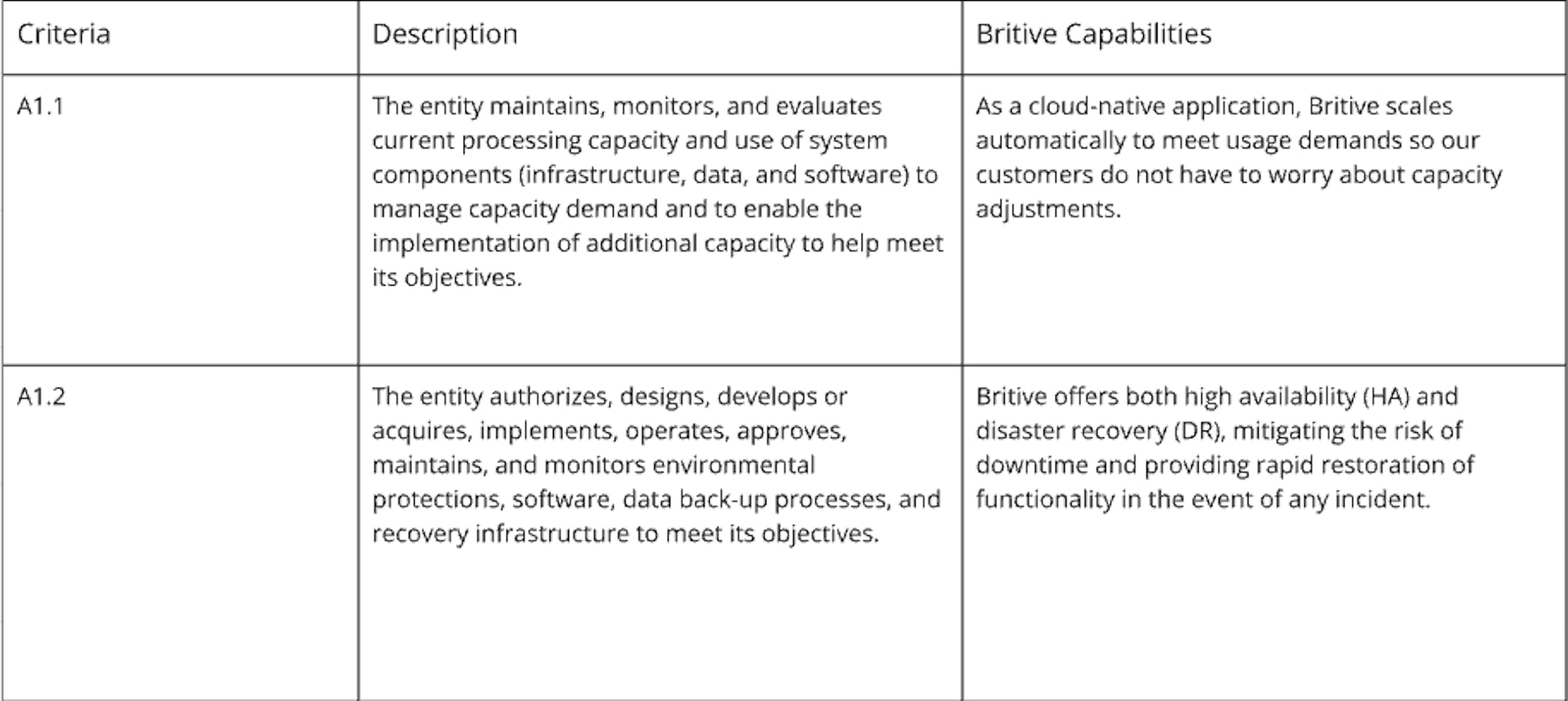
SOC 2 compliance isn't just about compliance for its own sake — it’s about strengthening security, reducing risk, and proving to customers that their data is protected.
Britive simplifies the compliance and access security process by eliminating standing privileges with just-in-time (JIT) access control and automating access provisioning and revocation. Reduce the attack surface with dynamic permissions management for all identities, both human and non-human. Simplify the audit process with centralized access logs across the entire environment and real-time visibility into privileged access activities.
Want to see Britive's capabilities in action in your own environment? Reach out to a member of the team for a demo.

