


Back to resources
Securing Data Privacy & Protecting Intellectual Property in GenAI-Powered Enterprises
February 2025 / 6 min. read /

The Rise of GenAI and the Data Privacy Challenge
Enterprises are increasingly leveraging artificial intelligence (AI) to enhance productivity across customer experience, sales, and marketing. Tools like retrieval-augmented generation (RAG), large language models (LLMs), and prompt engineering enable organizations to streamline operations, uncover insights, and make informed decisions.
However, the effectiveness of these tools also hinges on access to vast amounts of centralized data, often stored in modern data lakes and warehouses. This reliance on sensitive data raises critical security, privacy, and governance challenges.
The question is: how can enterprises safeguard proprietary data, prevent unauthorized access, and ensure AI models don’t inadvertently train on sensitive information?
A senior executive recently expressed both excitement and concern:
“AI tools are a no-brainer for boosting productivity, but they also pose significant risks if not secured properly. Security, privacy, and governance must be integral to the process—not an afterthought.”
The Data Security Challenge in GenAI Applications
AI tools depend on centralized data hubs to deliver value. Enterprises consolidate customer information, business insights, and other critical data into platforms like Cloudera, Databricks, and Xano. From there, AI systems generate predictions, reports, and actionable insights.
This centralization of sensitive information creates two primary risks:
- Preventing Data Breaches: AI applications and users need controlled access to specific datasets without exposing the entire system.
- Data scientists modeling financial forecasts for a U.S. bank should not access data from other clients.
- Support staff should not view company financials or confidential product roadmaps.
- Database engineers in Europe must comply with GDPR laws and access only relevant datasets. - Protecting Intellectual Property (IP): Proprietary data must not inadvertently train public LLMs, potentially exposing sensitive information or giving competitors an edge.
How Britive’s CPAM Solution Secures Data and IP
Britive’s Cloud Privileged Access Management (CPAM) solution addresses these challenges with advanced access control mechanisms designed for both human and non-human users. By leveraging just-in-time (JIT) access, Britive minimizes exposure to sensitive data without sacrificing operational agility.
Key Features of Britive’s CPAM
- Ephemeral JIT Access: Temporary, time-bound access ensures users and AI tools only interact with data they are authorized to use.
- Granular Permissioning: Fine-tuned control over access limits exposure and enforces least-privilege principles.
- Zero Trust Authorization: Every access request is verified to mitigate risks of unauthorized activity, regardless of where the request comes from.
- Automatic Revocation: Access is revoked immediately after a task is completed or a set period of time, closing potential security gaps from static access.
- Compliance and Governance: Detailed audit trails support compliance with regulations like GDPR and HIPAA.
Protecting IP with RAG and Prompt Engineering
To address the growing concern around intellectual property, Britive’s solution integrates with techniques like RAG and prompt engineering to ensure data security and governance:
- Retrieval-Augmented Generation (RAG): AI models retrieve specific data from private databases without exposing sensitive information to public models. IN combination with LLMs, RAG enhances the model’s output by providing real-world data.
- Prompt Engineering: Carefully designed prompts ensure proprietary data is used securely and does not train public AI models.
Together, these are some techniques allow organizations to harness the power of AI while safeguarding sensitive information.
Here’s a simplified diagram and description of each component involved in making the magic happen:
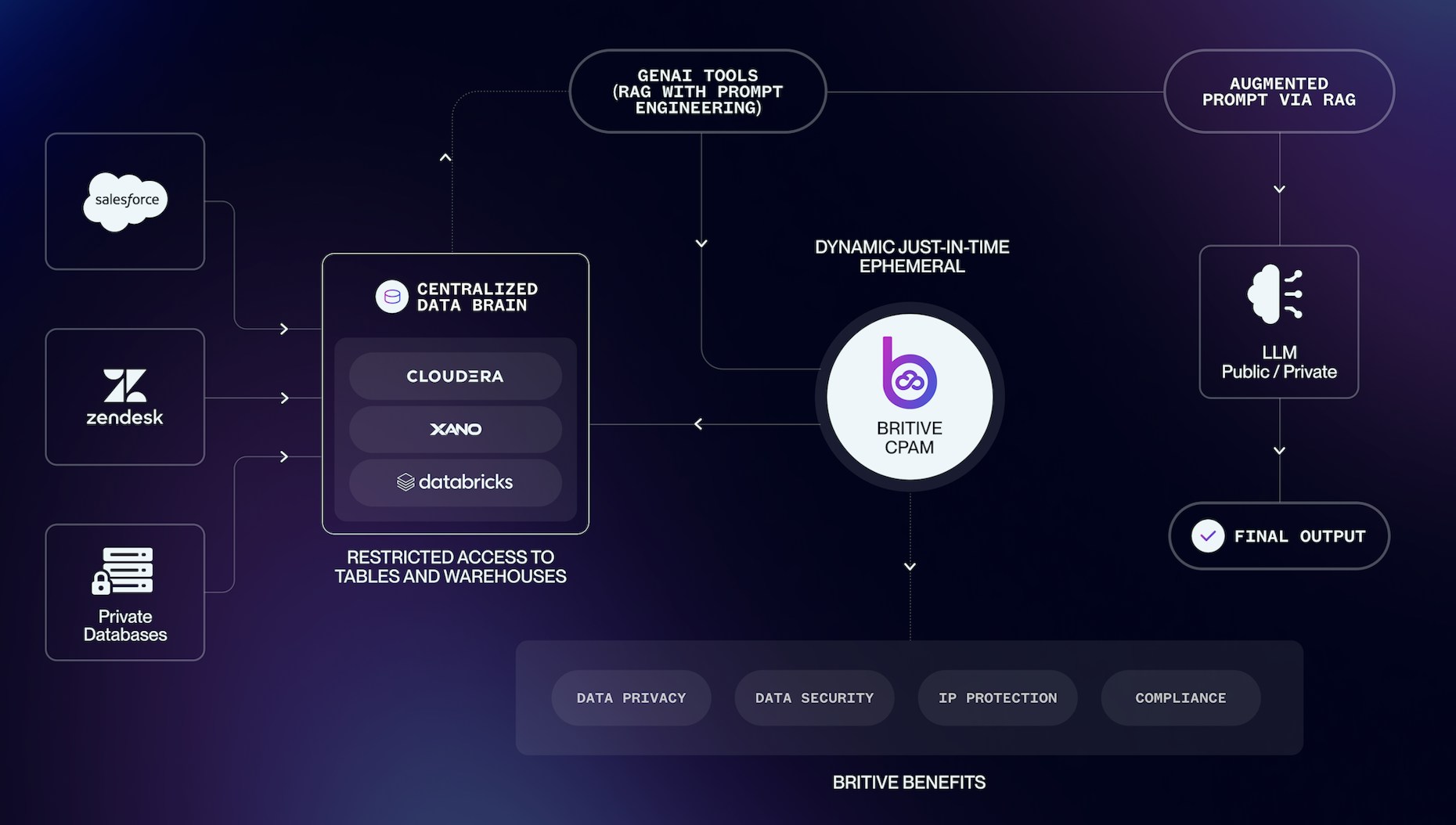
The Role of Britive in GenAI-Powered Workflows
Britive CPAM integrates seamlessly with modern AI workflows:
- Centralized Data Sources: Data lakes and warehouses consolidate business-critical information. This acts as the hub for all the ingested information and acts as the “brain” that AI applications and users interact with.
- AI Tools: Applications retrieve context-specific data using RAG, while prompt engineering ensures secure interactions while aligning with the task at hand.
- LLMs: Large language models generate accurate, task-specific outputs by integrating real-world data securely. LLMs use the data retrieved to generate intelligent responses, predictions, or content based on the prompts provided by the user.
- Britive’s CPAM ensures that both human users and any AI tools are granted access to specific tables or warehouses within the brain when requested. Access can be tightly controlled to ensure that only authorized users and systems can access the data, and that these permissions are revoked immediately.
The result of utilizing these systems in tandem is enhanced productivity with AI-generated insights that stay secure, private, and compliant.
Why Choose Britive for GenAI Security?
By combining advanced AI techniques with Britive’s CPAM platform, enterprises can achieve:
- Enhanced Data Security: JIT access minimizes the risk of breaches, granting access only upon request and for a finite amount of time.
- Stronger IP Protection: Prevents sensitive data from inadvertent exposure or use in training public models.
- Improved Regulatory Compliance: Detailed audit trails ensure compliance with privacy regulations and provide visibility into who accessed what data and when.
- Improved Governance: Granular control ensures that approved users only have access to the specific data required for their task, reducing the risks associated with over-provisioning.
The Bottom Line: Securing a GenAI-Powered Future
As enterprises increasingly adopt GenAI to drive productivity and innovation, securing data privacy and protecting intellectual property are non-negotiable.
Britive’s CPAM solution delivers a comprehensive framework for securing AI applications by enforcing zero trust principles, ensuring compliance, and protecting sensitive data — all while maintaining the speed and flexibility required in today’s business landscape.
Ready to secure your AI-driven workflows? Schedule a demo with our solutions architects today.
This blog was originally published on LinkedIn by Nauman Mustafa, Chief Strategy Officer at Britive.


