Back to resources
4 Key Takeaways from the New Gartner Report: Innovation Insight for Cloud Infrastructure Entitlement Management
July 2021 / 8 min. read /

Recently, Gartner released a new report, Innovation Insight for Cloud Infrastructure Entitlement Management, that is probably the most comprehensive look to date at the fast-emerging CIEM space.
Understanding Cloud Infrastructure Entitlement Management
The context is that managing cloud infrastructure entitlements is becoming a greater challenge due to their rapid increase in number and complexity, further exacerbated by the accelerating adoption of multi-cloud infrastructure as a service (IaaS) offerings. But it’s not just that more organizations are adopting the DevOps model for application and service development; there are several parallel trends or challenges that are driving demand for CIEM solutions. Gartner identifies the following:
Conventional approaches to access management aren’t workable in multi-cloud environments:
As cloud providers keep adding more services, the number of distinct entitlements has exceeded 5,000, on average, across different cloud service providers. This volume of entitlements becomes challenging to manage using traditional identity and access management (IAM) approaches like static policy and role-based access control (RBAC).
Organizations grant privileges and entitlements at a far higher rate than is warranted:
The vast majority of granted entitlements in IaaS are unnecessary. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises.
Organizations are on their own when it comes to managing entitlements and securing their cloud resources:
Among all cloud models, infrastructure as a service (IaaS) is the model for which the most access responsibility falls on client organizations. In IaaS — and platform as a service (PaaS) environments — managing access entitlements is a responsibility of the client organization alone.
How challenging exactly is privilege management for IaaS becoming? Gartner puts the situation in stark terms, setting out a strategic planning assumption that by 2024, “organizations running cloud infrastructure services will suffer a minimum of 2,300 violations of least privilege policies, per account, every year.”
A New Approach to Privileged Access
Gartner very much sees Cloud Infrastructure Entitlement Management as a logical progression from long-established identity and access management (IAM) and privilege access management (PAM) solutions built on least privilege approaches. In fact, in the paper’s section entitled The Future of CIEM, the authors note “Cloud Infrastructure Entitlement Management vendors are starting to add more traditional IAM capabilities (for example ... Britive’s JIT PAM approach)” referring to Britive’s just-in-time privileged access capabilities that make it possible for organizations to automatically grant and expire dynamic permissions to maintain a Zero Standing Privileges (ZSP) security posture.
But where IAM and PAM are designed primarily to secure data, apps, and users within the organization, CIEM is designed to manage permissions risks to prevent cloud breaches and data theft. So, what exactly is CIEM protecting, and where in the cloud is it providing this protection? Gartner sees three key categories of privilege entitlement aligned along with three operational areas: resources, services, and management.
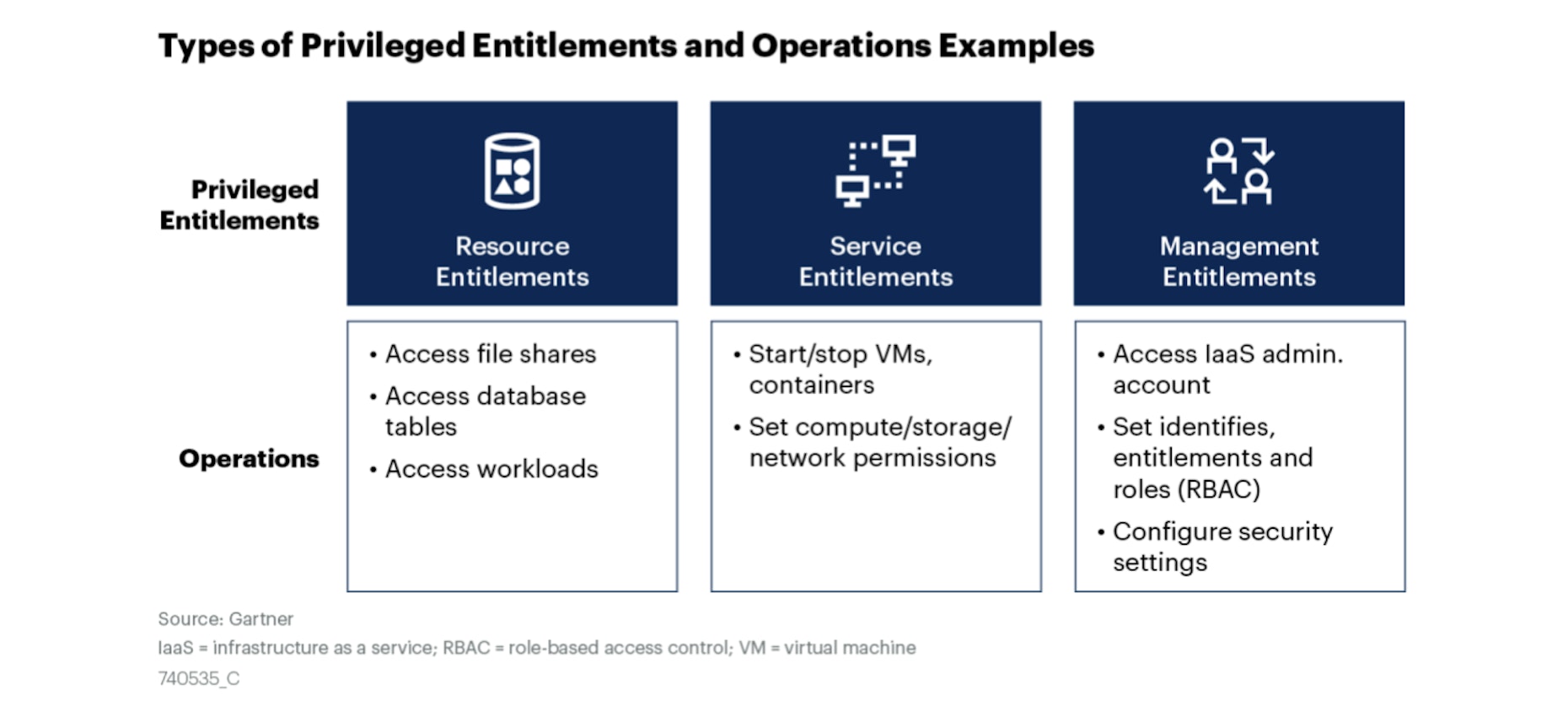
Essentially what Gartner is laying out here is that CIEM offerings need to be organized to mesh with the DevOps value chain. As the authors point out, DevOps use cases and infrastructure as code use very dynamic permissions and allow a bigger disruptive blast radius due to their automation capacities. Cloud Infrastructure Entitlement Management is a perfect fit within this structure because of its ability to govern access by granting visibility into unnecessary privileges, and refining policies, without disrupting developer flows.
Smartly, visibility is the first capability Gartner names in its list of the Four Core Uses of CIEM. Why visibility is a smart starting point is that virtually all else in the CIEM value proposition flows from the ability to see into existing entitlements and maintain visibility into entitlement operations over the long term. The authors explain that through access paths, it becomes possible to trace entitlement permissions visualizations in a graph, which are consistent across multi-cloud environments. When used correctly, a visualization graph provides crucial entitlement usage data:
- From a security principle standpoint: Where can this entitlement take this identity, and what can this identity do with the entitlements it has?
- From a resource perspective: What identities can access this resource, and what can they do with it?
Which leads to the second core use: privilege rightsizing. Once you can see into entitlements and permissions, it then becomes possible to revoke or curtail nonessential privileges. As the authors point out, the rightsizing process is an ideal starting point for organizations seeking to get better control over their entitlements and related processes. In short, rightsizing “is an easy, fast way to mitigate identity risks in multi-cloud environments, which would be impossible to achieve using only static data ... If it sounds almost too simple, it’s because it is.”
Gartner’s third core CIEM functionality is advanced analytics. Beyond removing dormant entitlements, there are many other types of access anomalies that CIEM solutions are effective at tracking and—in some cases—automatically mitigating through autonomous governance, machine learning (ML) and artificial intelligence (AI). To understand how this works, we’ll quote the report at length here:
The concept of autonomous governance… requires predictive and prescriptive analytics capabilities working together with AI (in other words, advanced analytics), using quantitative methods to either recommend or execute autonomous actions. More sophisticated anomaly detection strategies in advanced analytics are possible through ML, which can be “taught” usual patterns and how to remediate, applying automated action, to mitigate risks when unusual usage of access is detected. Instead of relying on the definition of enterprise roles for every possible combination of fine-grained entitlements in the cloud, CIEM can be applied to calculate rules based on exceptions.
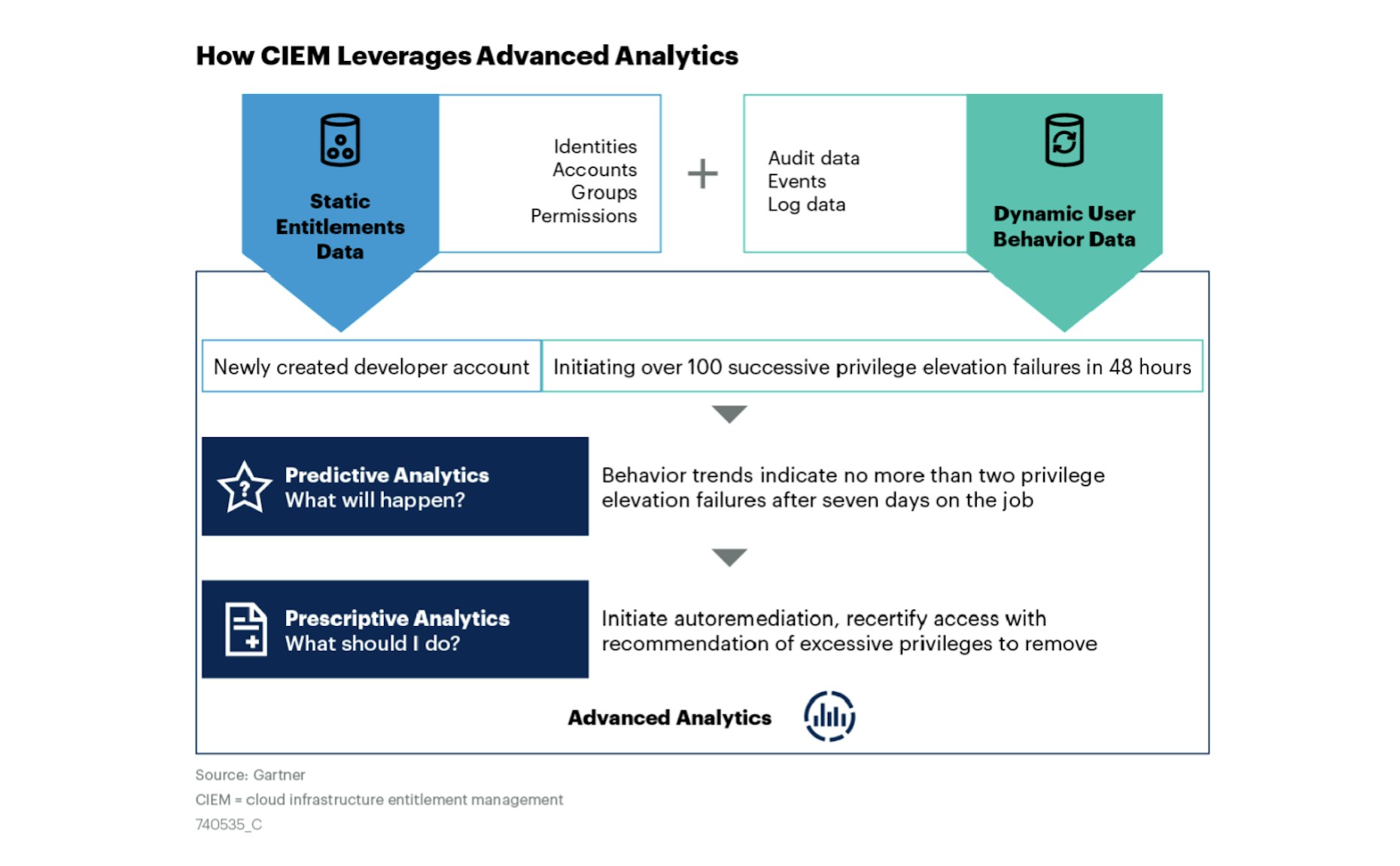
This is basically an automated version of a “see something / say something” process. Here at Britive, we like to cite a couple of customer scenarios where our platform could employ analytics to mitigate risks. There’s the obvious instance where a user with privileges to your AWS instance logs in and immediately deletes 40 data buckets. Risk scoring is rightly going to identify that behavior as highly suspicious, and auto-mitigation is likely to kick in.
A more nuanced example where least privilege access can be brought to bear to reduce exposure to vulnerability: Your DevOps team has quickly grown to 100 users. Of that total, 10 users are making full use of their access privileges. The other 90 are using only 15% to 20% of their privileges. It’s a situation where 90% of your DevOps team is overprivileged; your exposure is needlessly broad and should be remedied.
The last of Gartner’s four core CIEM functions: compliance automation. The authors point out that most CIEM tools offer ways to continuously monitor for gaps between a) the desired security policy, b) the intended identity security posture (what the developer/DevOps team intended) and c) the actual identity security posture observed at runtime. With the CIEM solution focused on identity controls:
... automation of compliance can then be provided by detecting and remediating policy drift. Because of the different maturity stages of analytics provided by CIEM vendors, not all tools offer this capability for dynamic policies (policies defined by user behavior analysis, for example). However, at least a minimum basic compliance automation based on static policy drift monitoring should be expected.
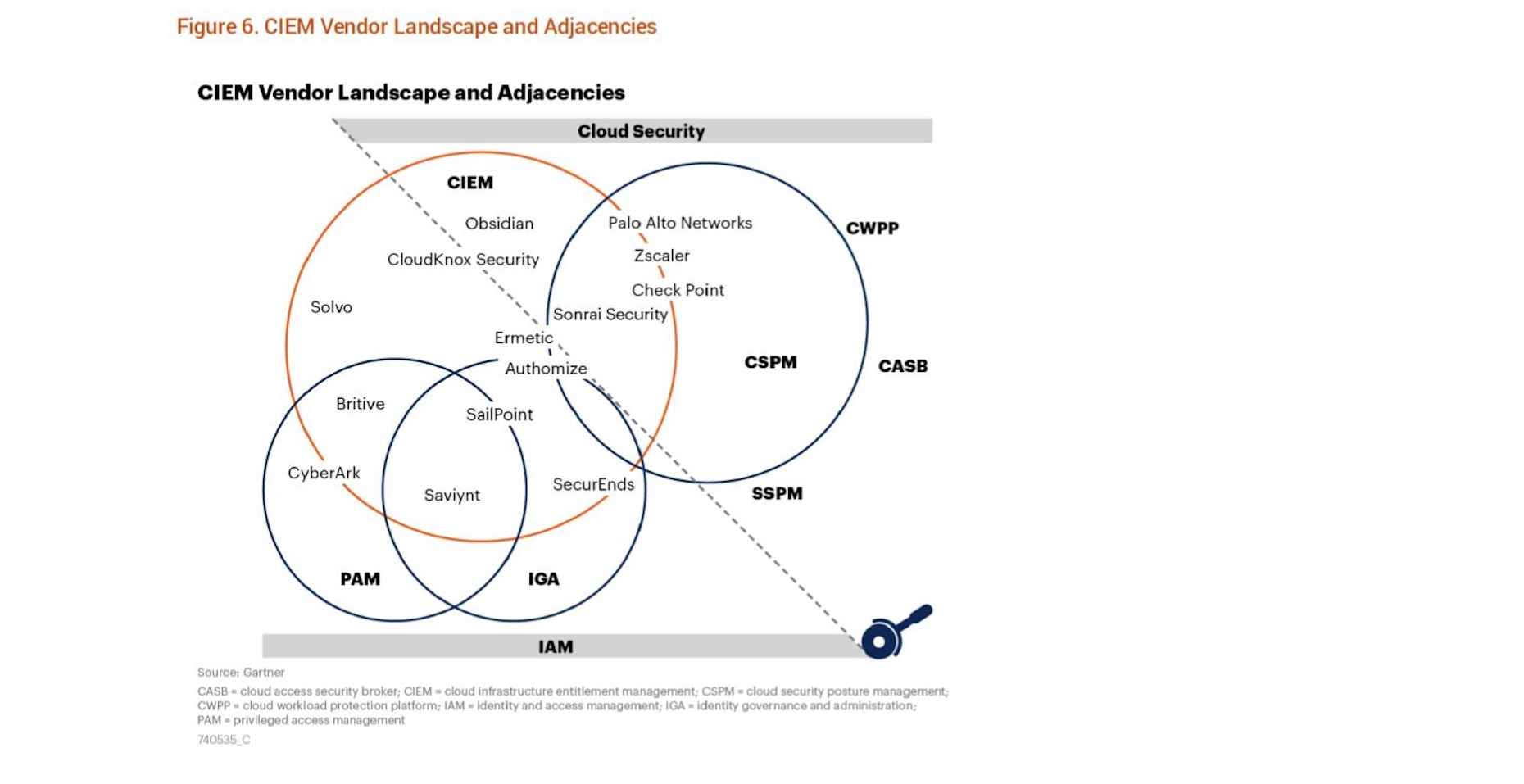
Gartner closes out the paper with some thoughts on how CIEM has quickly evolved to meet very specific security needs for organizations with complex cloud operations and provides specific recommendations for decision-makers who are considering CIEM solutions. There’s also a helpful Magic Quadrant-style graphic identifying the major players in the space and some accompanying thoughts on how CIEM will progress and grow in the years ahead.
As you’d expect with a Gartner Innovation Insight paper, it’s a quick read, yet highly informative.