


Back to resources
Microsoft Acquired CloudKnox – Here’s How Just-In-Time Permissioning Can Help Keep Your Multi Cloud Environment Secure
July 2021 / 4 min. read /

A round of applause for the CloudKnox Security team. Congratulations on the acquisition by Microsoft!
But as we celebrate this milestone, it’s important to consider how organizations that use the CloudKnox solution will be affected.
- Can you continue to expect the same attention and support?
- Will you have to commit to other Microsoft products?
- What will happen to CloudKnox’s product roadmap – especially as it relates to cloud platforms that are Microsoft competitors – and how will it align with your existing cloud strategy?
Such questions and uncertainties mean it is time to reassess your cloud privilege management strategy and consider alternatives.
According to CloudKnox, more than 90% of identities only use 5% of granted permissions. That results in 95% of all permissions being unused, unchecked, and vulnerable to employee error or hacker exploitation.
What’s more, the company’s recent State of Cloud Entitlements Report found that:
- In Amazon Web Services, two-thirds of enterprises have Elastic Compute Cloud (EC2) instances with access to all Simple Storage Service (S3) buckets.
- In Google Cloud Platform, more than 50% of enterprises have project-wide Secure Shell (SSH) keys enabled for virtual machine instances.
- In Microsoft Azure, more than 85% of enterprises have over-permissive identities left orphaned after projects are terminated.
These gaps, left unchecked, can leave organizations at the increased vulnerability of ransomware and other attacks resulting from exposed account credentials.
Britive has a solution to this problem and has programs to help you transition from CloudKnox to our cross-cloud privilege management platform.
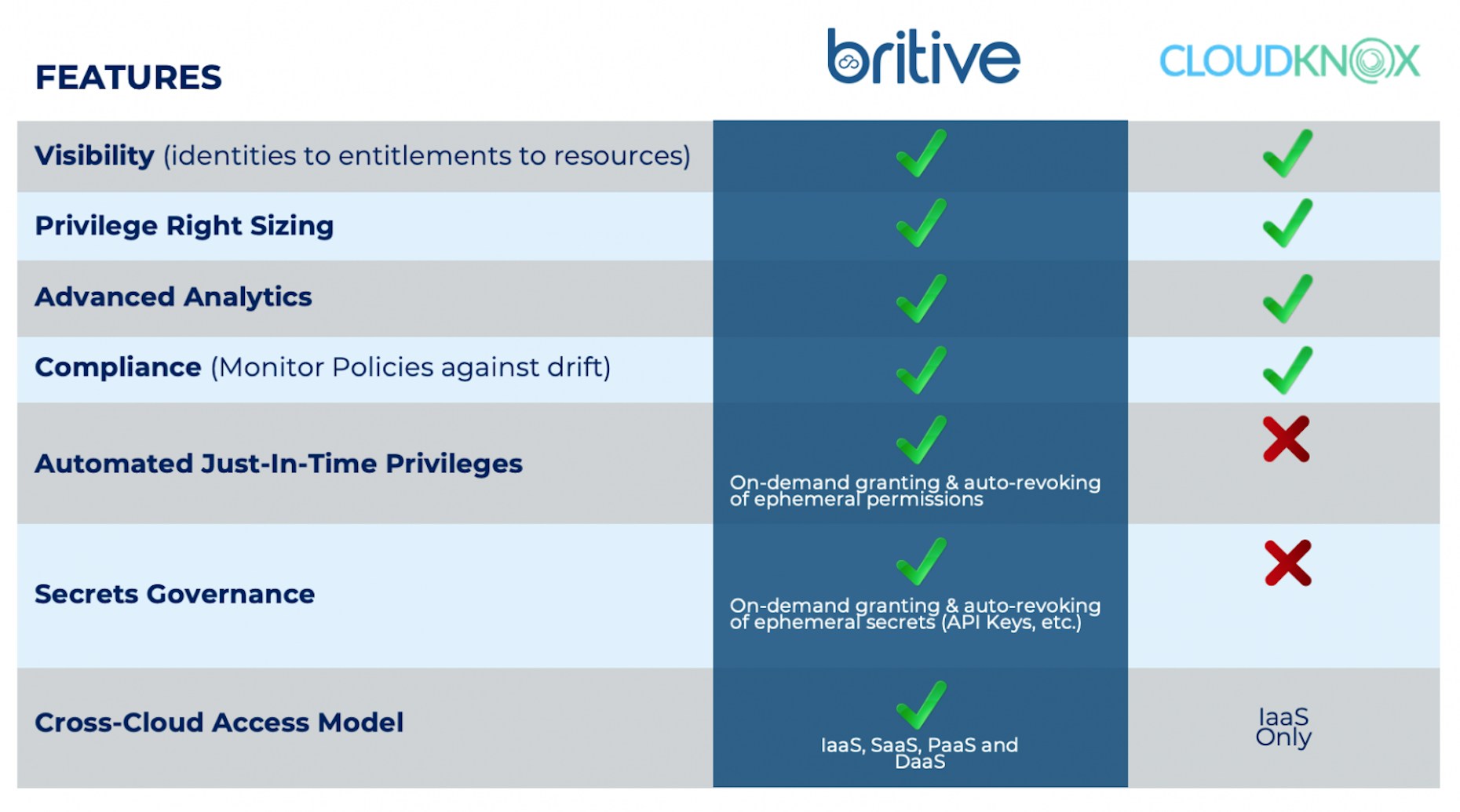
Conventional approaches to access management aren’t workable in multi-cloud environments. An organization that grants elevated permissions only when necessary, and simultaneously does not impede business growth or DevOps, stays in front of the competition and keeps its multi-cloud environment secure.
In fact, per Gartner’s latest report, Innovation Insight for Cloud Infrastructure Entitlement Management:
As cloud providers keep adding more services, the number of distinct entitlements has exceeded 5,000, on average, across different cloud service providers. This volume of entitlements becomes challenging to manage using traditional identity and access management (IAM) approaches like static policy and role-based access control (RBAC).
You can maintain Zero Standing Permissions (ZSP) with Britive’s Just-in-time (JIT) permissioning and secrets grants.
Unlike traditional IAMs and PAMs, and CIEM solutions like CloudKnox, Britive’s Cloud Privilege Management Platform addresses a key cloud access security gap: the elevated exposure and risk associated with maintaining standing cloud access privileges and over-privileged cloud accounts.
Through the application of a unified access model across IaaS, SaaS, PaaS, and DaaS service, the cloud-native, 100% API-based Britive platform (no agents gateways or proxies) provide temporary Just-in-Time privilege grants.
The on-demand granting of elevated privileges for human and non-human users that are automatically revoked after a set period of time enables companies to minimize their attack surface through maintaining a state of Zero Standing Privileges.
In addition, organizations can ensure that employees and contractors are granted the right level of privileges when onboarded, constantly right size those privileges over time, enforce access policies, and fully offboard users when they leave the organization. This enables IT teams to maintain Least Privilege Access (LPA) throughout the cloud identity lifecycle and minimize the potential blast radius of internal threat actors.
Finally, Britive integrates seamlessly with CI/CD automation software such as Jenkins and Terraform, empowering cloud application development teams to add access security to their development pipeline without introducing management complexity or creating a security speed bump – a common challenge for traditional IAM and PAM solutions, and a key impediment to building secure, high-velocity DevSecOps processes.
With Britive you can achieve Zero Standing Privileges for human and machine identities and maintain true Least Privilege Access cross-cloud: IaaS, SaaS, PaaS and DaaS.
Contact us today and maintain true Least Privilege Access cross-cloud with Britive’s Just-in-time permissioning and secrets grants:
Sales@britive.com.">Sales@britive.com.
Remember, only Britive’s Cloud Privilege Management Platform addresses the elevated exposure and risk associated with maintaining standing cloud access privileges and over-privileged cloud accounts – a key cloud access security gap.

