


Back to resources
Art Poghosyan, CEO & Co-Founder of Britive, on How the Pandemic Accelerated Cloud Adoption
April 2022 / 9 min. read /

This article originally appeared in Cyber News.
Cyber threats are only improving and it’s only getting harder to prevent them, especially when the attack surface has broadened drastically after the switch to remote work.
With various threats lurking in the corners of the Internet, it is virtually impossible to prevent them from infecting devices without any security tools, especially for companies of any size.
While ordinary users protect themselves with antivirus software and similar measures, businesses make use of cloud and other solutions.
For this reason, to learn more about cloud solutions, their benefits, and cybersecurity trends, we invited Art Poghosyan, the CEO of Britive, a company which effectively takes care of a multi-cloud environment.
Britive Co-Founder & CEO Art Poghosyan

What was your journey like since your launch? How did it all begin?
My two Co-Founders have dedicated several years to identifying and resolving security challenges in the on-prem identity and access management space. A few years ago, we realized that the shifting of workloads to the cloud presented the greatest risks to organizations. The driving force behind those risks is the proliferation of identities and permissions cross-cloud that must be secured. That was never a major concern during the on-prem days.
We identified three significant challenges and committed to solving them. The first is the basic need to automate the process of uncovering and managing thousands of permissions across SaaS, IaaS, PaaS, and DaaS. A tremendous amount of SecOps, CloudOps, and DevOps teams are relying on old school spreadsheets to accomplish this, which is both time-consuming and error-prone. Add to that the fact that each cloud service has its access logic. If you don’t use automation, it must be painstakingly learned before being managed and secured.
We identified the proliferation of permanent standing cloud permissions as an open invitation to threat actors to exploit identity-based vulnerabilities. The infamous SolarWinds attack is a classic example of cloud account credentials being compromised by malicious actors to access sensitive data.
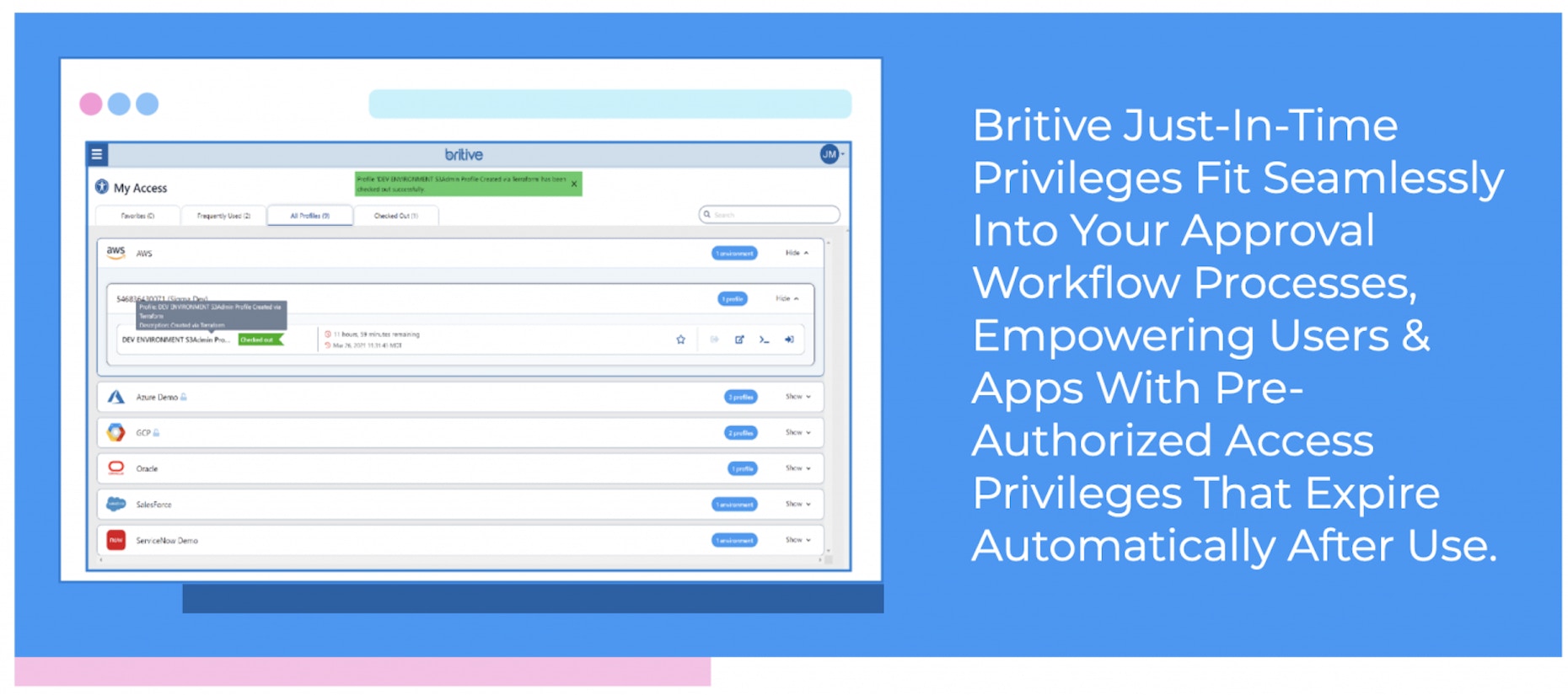
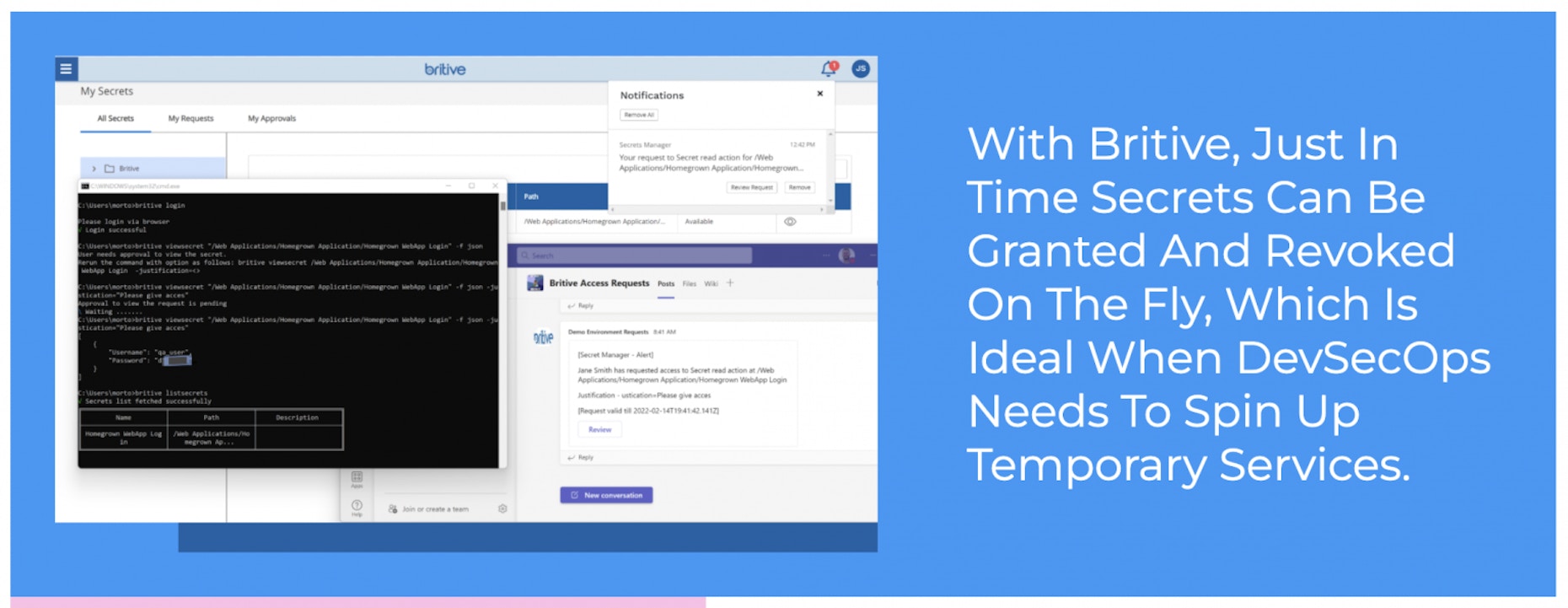
Furthermore, we identified the demand from DevOps teams to help them build access security into their CI/CD processes without adding additional complexity or management overhead. From our experience, we saw that DevOps teams are often resource-constrained and have to remain singularly focused on the development process. Given the fact that developers – like their cloud admin colleagues – hold elevated privileges, their accounts are considered high-value to threat actors and therefore, in need of the highest level of strong security. By enabling self-service just-in-time (JIT) permissioning, you can secure DevOps users with minimal overhead. Additionally, DevOps needs to manage secrets dynamically to more effectively secure non-human identities, such as APIs and other automated processes. We enable DevOps to spin up temporary services swiftly by generating JIT secrets on the go.
What are the major challenges companies face with securing the cloud? Has the pandemic made it worse?
Undoubtedly, one of the biggest challenges facing cloud security pros today is the fact that the “cloud-native security stack” wasn’t logically planned or built as an integrated entity. It came together and grew from a collection of security point-solutions that were originally designed to address various security needs. Today, we are faced with a confusing hodge-podge of CSPM/CIEM/CASB/PAM/IAM tools and more to secure cloud services. There’s some overlap and some have been repurposed from on-prem solutions that are now imperfectly retrofitted for the cloud. Others leave holes in security between them and adjacent technology solutions. But quite possibly the biggest challenge is that they often provide limited insight or controls over identities and permissions. Our solution is designed as a cloud-native access management platform that adds its unique JIT permissioning and secrets governance capabilities plus complementary capabilities that span categories like the CEIM, IGA, and PAM, among others.
The pandemic has accelerated cloud migration, with more and more companies going deeper and deeper into the cloud. This has resulted in a rise in breaches; Solarwinds is a case in point. CISOs are in constant fear of what’s ahead and whether they are prepared to fare the next “big one.”
Can you tell us a little bit about your platform? What are its key features?
One of Britive’s core value propositions is to provide cross-cloud visibility and automated controls for cloud permissions. As I mentioned previously, security teams face managing thousands of permissions/privileges across all the cloud services a company uses. It’s an arduous task that is still in many cases done manually, which presents a strain on resources.
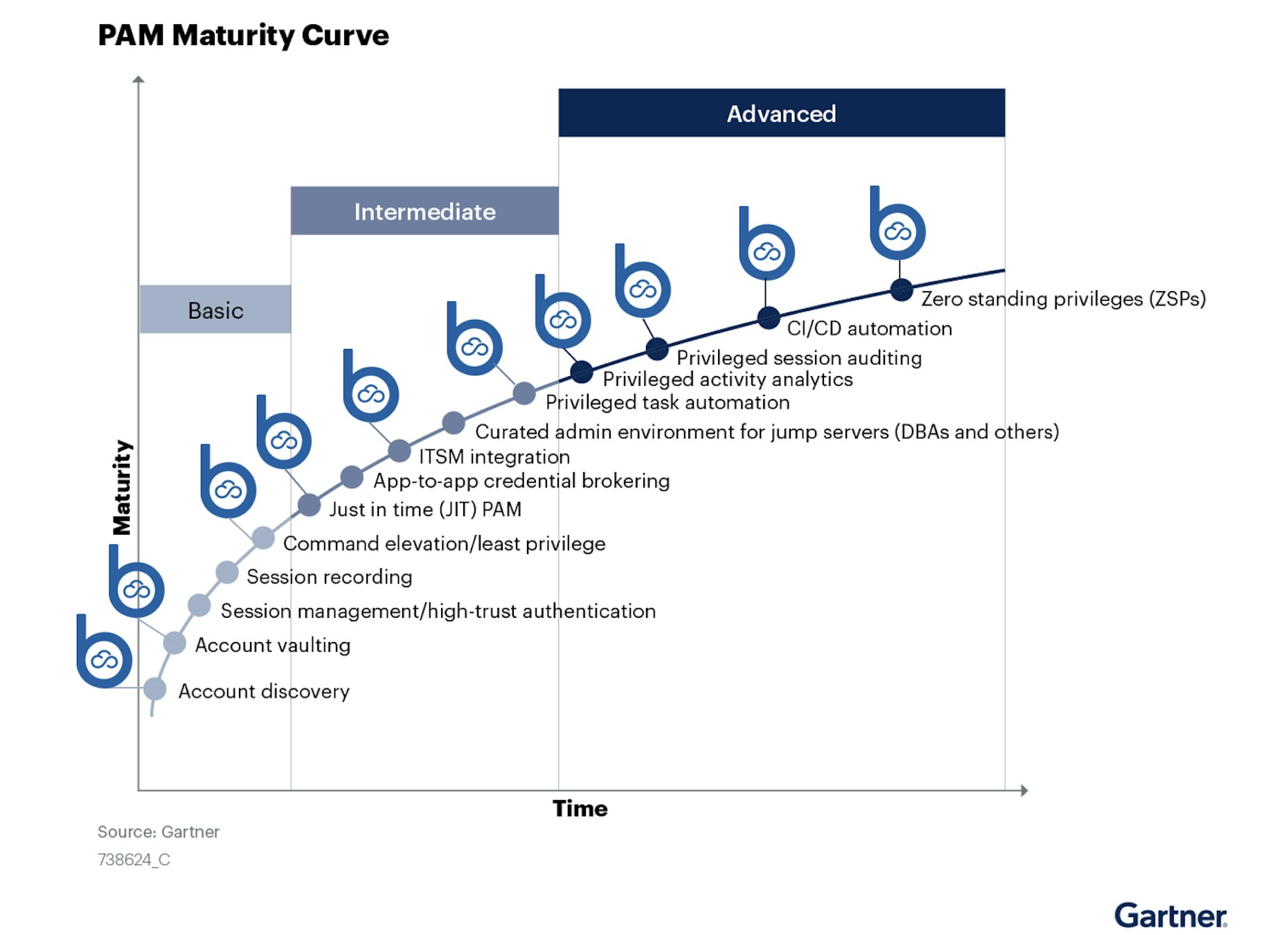
Britive also assists companies with enforcing Zero Standing Privileges (ZSP) through Just in Time (JIT) permissioning where permissions are only granted for a set time period and then revoked at the end of the cloud session. By doing that, we minimize the organization’s attack surface. It is easy to understand why this needs to be a priority when you consider that cloud access threats have now surpassed those caused by malware in recent years.
By enabling self-service JIT permissioning, we secure DevOps users with minimal overhead. Additionally, DevOps needs to manage secrets dynamically to more effectively secure non-human identities, such as APIs.
An organization can use Britive in a wide variety of ways. Many – if not most – companies find specific value in our unique JIT permissioning, which is useful in both saving costs by minimizing or eliminating standing privileges and multiple accounts (i.e., an admin who must otherwise maintain both non-privileged and privileged accounts to maintain SoD) and for enhancing security by keeping the company’s attack surface to a minimum through enforcing ZSP.
We also feel strongly that Britive can be indispensable in the efficient onboarding and offboarding of employees and contractors. It ensures that cloud users have the right level of permissions when they start work, continually have their privilege right-sized during their employment, and their permissions are fully and quickly deprovisioned when they leave the organization.
Many companies have chosen cloud solutions to enhance security, but is it truly a “one-size-fits-all” option? Are there any details that might be overlooked?
Details tend to be overlooked as a company adopts multiple cloud environments. To be sure, plenty of security tools are available that help manage identities. But too many have limited cross-cloud capabilities and end up standing in the way of a company’s business priorities.
Cloud ecosystems are complex; thousands of human and non-human identities must be authenticated and granted specific permissions. As a company scales across CSPs and various cloud applications, individual security products become difficult to leverage, users cannot be efficiently managed, and the security tools used to protect an environment impede a developer’s ability to build quickly.
For too long, a “one-size-fits-all” solution was out of reach. Britive solves that problem.
What are some of the most serious cyber threats that you think will become prominent in the next few years?
Hardcoded secrets, standing permissions, and a broad attack surface will allow attackers to compromise users, gain privileged access, and seize control of a company’s cloud environment.
That’s why businesses must pivot from a remediation mindset to a proactive posture. In the cloud, security must align with business priorities. The good news is that Britive provides security without a traditional security experience; organizations can eliminate hardcoded secrets, remove standing permissions, and minimize the attack surface – all while continuing to scale.
Cyber threats are not going away. But with a proactive approach and the right tools, companies can scale, gain agility, and accelerate production.
In your opinion, why do you think certain companies are not even aware of the dangers hiding in their own networks?
Multi-cloud environments are highly complex ecosystems. Each service has certain requirements and nuances. Take identity and access, for instance. Security teams currently manage users manually through spreadsheets, which is time-consuming and error-prone. The ability to automatically discover identities and their permissions is essential.
Besides moving to the cloud, what other security practices do you think are essential for businesses nowadays?
First and foremost, companies should adopt the principle of zero-trust security in multi-cloud environments. But merely enforcing least privilege access (LPA), as many traditional IAM, PAM, and CIEM solutions do, won’t cut it. If an identity is compromised, or there’s a misconfiguration, bad actors can still access your environment and wreak havoc.
Secondly – maintain zero standing privileges and dynamic temporary access because, in the event of a security incident, the bad actor has no place to go – permissions don’t exist and the ability to move laterally across an environment is stifled. Zero trust is thereby maintained when it comes to elevated access privileges.
Finally, companies should also remove the complexity and minimize the time it takes to secure identities and permissions across multi-cloud environments, including IaaS, PaaS, SaaS, and DaaS services.
As for individuals, what security measures do you think every casual Internet user should have in place?
Just like businesses, individuals need to protect their user credentials. Be mindful of secrets sprawl – passwords, tokens, notes, etc. – anything you use to access data and cloud environments should be regularly changed to ensure maximum security.
For individuals doing business in the cloud, take stock of your attack surface, review where you work and how you access and manage your data, take action to eliminate vulnerabilities, and reduce the opportunities an attacker has to exploit your business.
Share with us, what’s next for Britive?
Britive will continue to build the most comprehensive platform solution for enterprise organizations to help them continue their cloud journeys and meet critical business objectives while our technology ensures their cloud identities (human and non-human) are secured.

