


Back to resources
Minimize Your Blast Radius by Decoupling Cloud Permissions
March 2022 / 3 min. read /

Elevate Cloud Permissions Management
Many customers have been asking Britive to help eliminate the standing (24x7x365) "SuperAdmin" privileges from critical cloud platforms like Okta, Salesforce, Snowflake, and Workday.
Why?
Because in the cloud, bad actors actively target standing privileges to gain access to an organization’s environment.
Most organizations know that standing privileges increase your attack surface, but managing elevated privileges cross-cloud is time-consuming, disruptive, and prone to error.
- Cloud adoption means growth, sometimes on a massive scale. It’s extremely difficult to gain visibility and control of elevated privileges when thousands of human and non-human identities need access across various cloud apps and platforms
- Security tools that slow down DevOps impedes your organization’s ability to meet business priorities
- Because managing permissions cross-cloud is complex and error-prone, users are granted standing elevated permissions that are susceptible to hacks.
So how do you achieve true business security in the cloud? By minimizing standing privileges and enforcing Defense-in-Depth through a layered security model.
Cloud Permissions
Britive addresses this urgent need by complementing authentication, e.g. Multifactor Authentication (MFA), with Just-in-Time (JIT) Authorization.
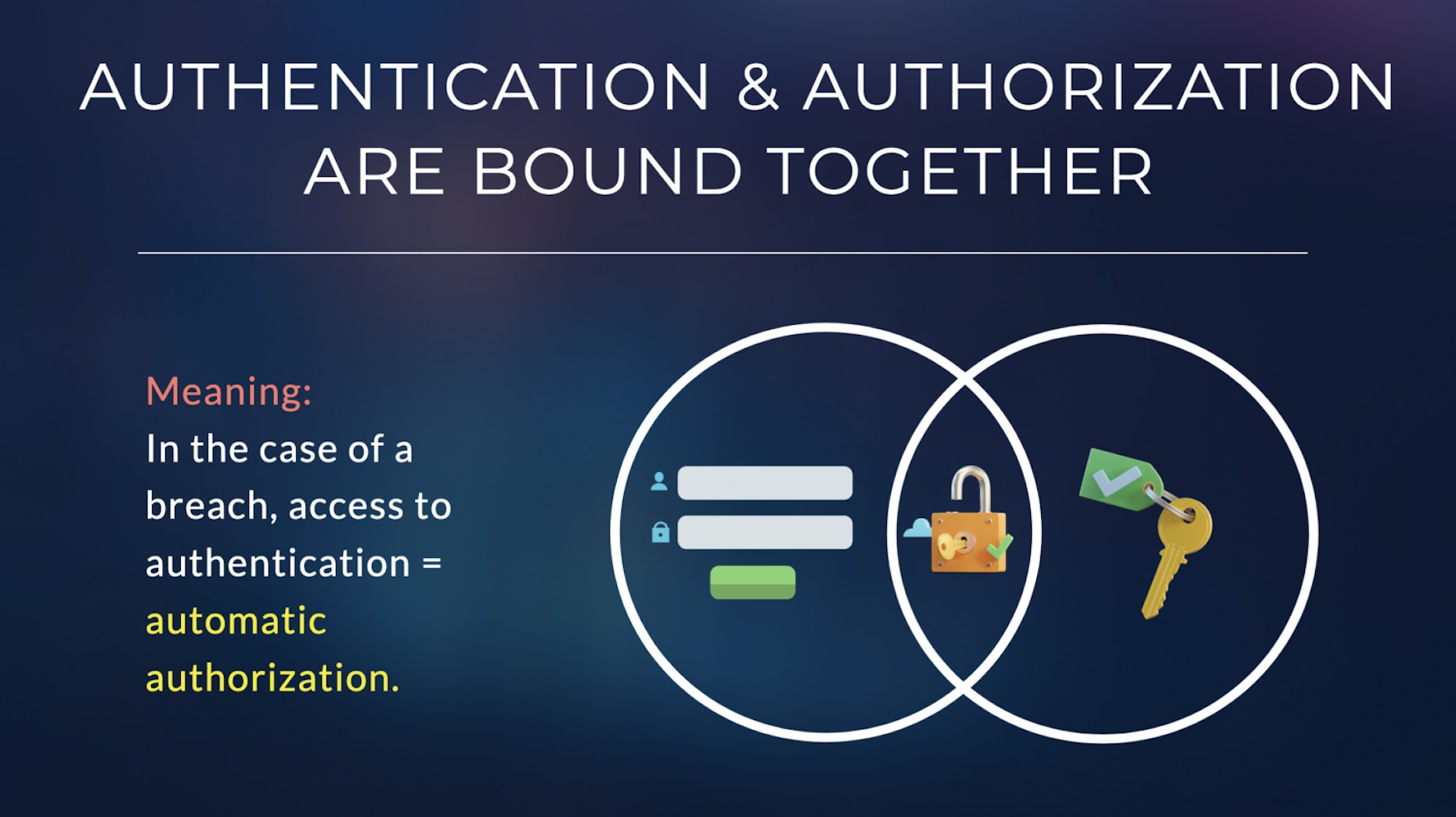
Typically, cloud security binds authentication and authorization together. When human and/or non-human IDs are authenticated, their permissions are automatically authorized. This gives the user elevated standing privileges to access data, apps, active directories, and more.
Attackers exploit this process to access cloud apps and platforms. While this is not a new tactic, the stakes have never been higher. When an attacker steals the keys to the kingdom, organizations have few options to retake control.
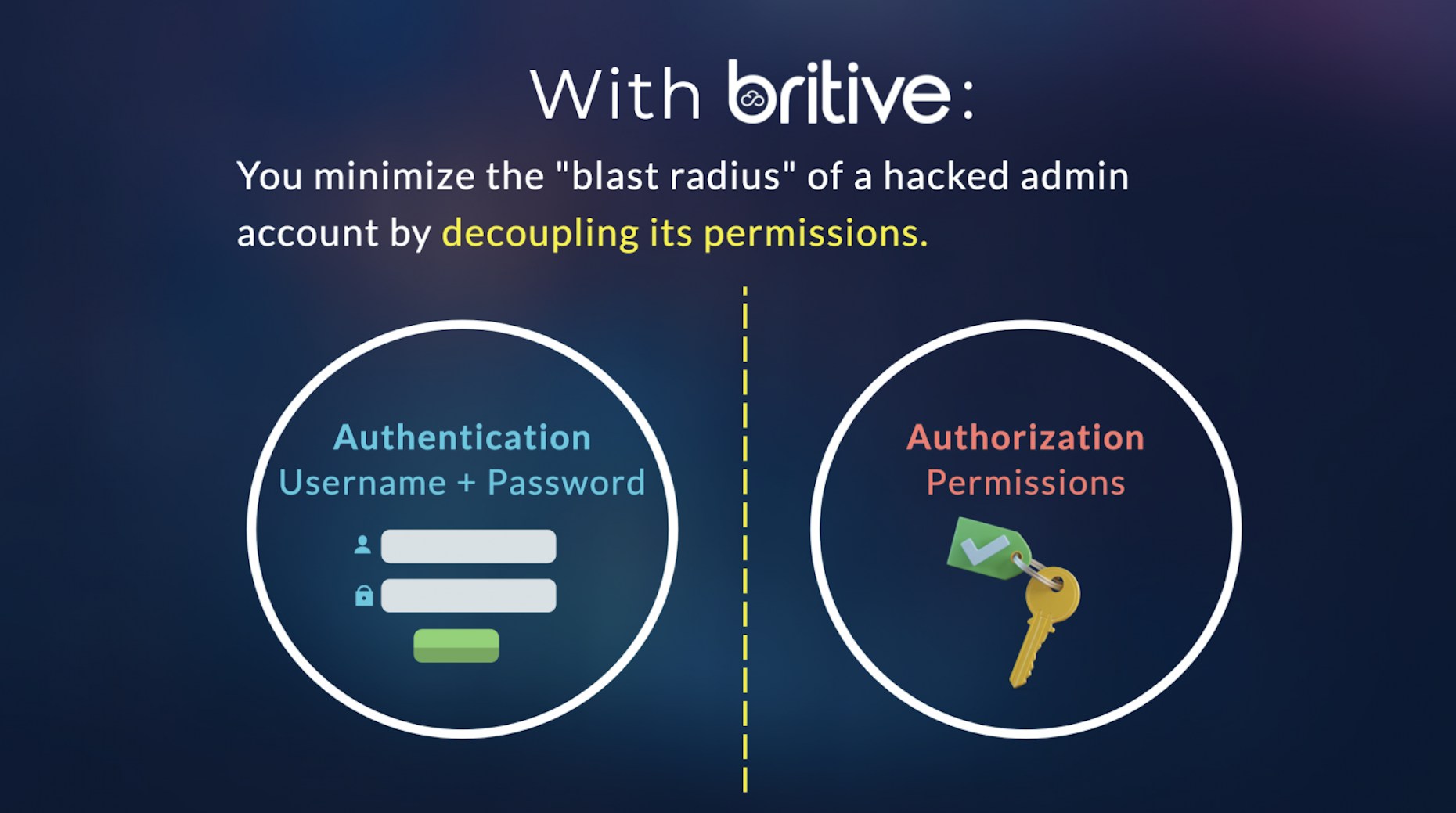
Britive keeps Authentication and Authorization separate by granting and revoking Just-In-Time privileges after the user has been authenticated. Meaning: Authenticated users must be authorized in order to access elevated privileges. In the case of a breach, access stops at authentication.
Organizations minimize the “blast radius” of a hacked admin account by decoupling its permissions.
Remember: Authentication is a core defense that is among the most effective ways of preventing account takeovers. But recent events show that it is not much of a hurdle for some hackers to clear. In the past few months, suspected script kiddies like the Lapsus$ data extortion gang and elite Russian-state threat actors (like Cozy Bear, the group behind the SolarWinds hack) have both successfully defeated the protection.
Organizations must eliminate standing privileges and enforce Defense-in-Depth through a layered security model (strong authentication + JIT privilege authorization).
The Britive Dynamic Permissioning platform complements your existing security tool or serves as an out-of-the box solution. It is a lightweight and dynamic solution organizations can use regardless of where you are on the cloud journey.
Here's how decoupling authentication vs authorization drives our unique just-in-time permissioning.

