


Back to resources
GCP Security Requires Additional Cloud Permissioning Safeguards - Here's How
July 2022 / 6 min. read /

While there may be questions around GCP security, there's no question that GCP as a whole is an ideal cloud platform for development velocity. According to Stack Overflow’s Developer Survey, 66.8% of developers working on GCP expressed high satisfaction with their ability to deliver apps efficiently. That’s great news for organizations in the business of developing software for customers in telecommunications, retail, manufacturing, financial services, and other industries.
It makes perfect sense. When DevOps teams can collaborate and build without much restriction, delivery times accelerate and overall market velocity increases. Human and synthetic users retain the permissions they need to access the resources to get the job done. From a business perspective, GCP is a win-win. It is fast and collaborative in nature, has a pleasant user experience, and is constantly evolving its capabilities.
But what about GCP security?
What native identity management tools does GCP provide that ensure all identities—human and nonhuman—do not increase an organization’s attack surface?
*The following diagram illustrates permission management in IAM.
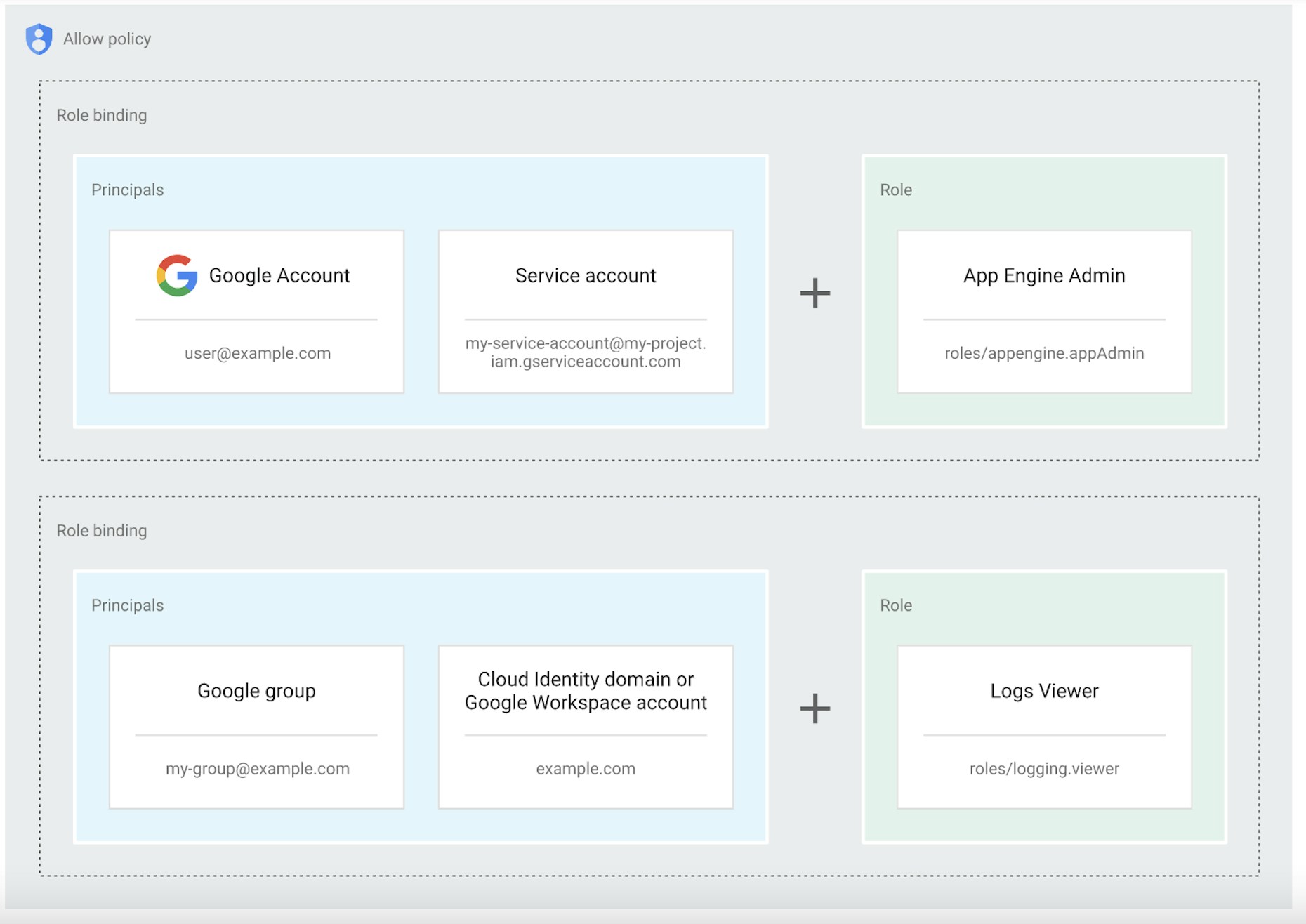
Let’s take a look at what GCP offers and where vulnerabilities might put a company at risk.
GCP Security Risks
While privilege access is a good thing for developers, it is a serious concern for security teams. Google knows this. As a result, it has built a fairly robust identity and access management (IAM) solution that’s designed to minimize exposure and control access.
Adhering to the principle of least privilege access, Google recommends that all users should be granted enough access to complete everyday tasks and nothing more. Administrators are responsible for assigning access to various users and groups by defining functional roles. In best practice, an organization’s security policies dictate the level of access to each of these roles.
Organizing access based on policy lets administrators understand the hierarchical approach to implementing IAM. Fundamentally speaking, this is an industry validated posture to adopt. However, given ever-expanding identity lifecycles in the cloud, complexities arise and too often, administrators and users are left with elevated standing privileges. Standing privileges represent a major threat to an organization; attackers recognize these opportunities and target them aggressively.
What this means is that as a company leverages GCP more and more, as it scales and relies on additional administrators, users, and groups to satisfy key business drivers, it simultaneously catapults security risk into a higher level by expanding its attack surface.
Google’s identity solution does a good job of helping administrators organize various levels of access, but it would benefit from a solution that eliminates standing privileges and grants access on-the-fly.
What’s the way forward?
*The following video illustrates Just-In-Time permissioning on GCP.

Improve GCP Security
Here are three ways to improve identity access management in GCP:
1. Use Just-in-Time (JIT) privilege grants
Cloud security teams now recognize that JIT privilege grants are an excellent way to minimize an organization’s blast radius. When an authenticated user needs access, the user must first be authorized; only when authorized does the user’s access request move up the chain. Authorized users are granted access for a limited period of time. When the user completes the task or time expires, access is revoked. Ephemeral access facilitates zero standing privileges.
2. Implement cloud secrets management
The keys that GCP manages are encrypted by default, but organizations may wish to make objects in buckets readable to the public, which means Google would decrypt the data. As a result, these keys are exposed and vulnerable to attack. What’s more, API keys, when tied to projects in GCP, are not programmatically monitored. There is no automatic way to inventory API keys for when they are created, used, and deleted. In secure cloud environments all secrets should be monitored, and, like JIT privilege grants, issued and revoked automatically only when an authenticated user is authorized.
3. Improve cloud visibility
We are focused on GCP here, but the reality is that many companies also use Azure, AWS, and any number of SaaS products. So while it is expected that visibility is strong in a single environment, cross-cloud visibility is ideal. GCP does provide “fine-grained access control and visibility for centrally managing cloud resources” but it could improve its ability to identify elevated permissions, standing permissions, and comprehensive user behavior. These capabilities let organizations make informed decisions: privilege right-sizing and data analytics not only augment security practices, they empower teams to make strategic business decisions based on how access is used.
GCP Security—Working Together
There’s no doubt that GCP takes security seriously. There’s also plenty of reasons developers love its production environment and collaborative workflows. But as cloud usage evolves and matures, as teams grow and companies scale, adding additional security to protect the keys to the kingdom just makes sense.
Evidence exists that companies feel confident about using GCP to expand offerings. Take Target, for example. The retail giant has more than 5,400 apps in its eponymous application platform. Here, GCP serves as a highway for developers to build apps and make them available as quickly as possible.
Do those developers have elevated standing privileges? Most likely.
How vulnerable are they to a breach? Only time will tell.
The bottom line is that JIT privilege grants, dynamic secrets management, and broader visibility into user behavior would reduce risk without impeding delivery times—full stop.

GCP states that its customers span top players across industries:
- 8 of the top 10 telecommunications companies
- 7 of the top 10 software & internet companies
- 7 of the top 10 media & entertainment companies
- 7 of the top 10 retail & CPG companies
All companies want to protect access to their cloud environments. And the ones listed above no doubt have effective security policies in place. But when it comes to securing public clouds—in GCP specifically—we are still in the Wild West.
Conclusion
Companies understand that success in today’s dynamic digital market comes from leveraging products and services that align with business objectives. Security needs to be one of those objectives—and access management should be accepted as part of the cost of doing business in the cloud.
Standing privileges for admins and app developers that remain vulnerable to exploitation 24/7 massively increases the blast radius of your human and machine users. Limited visibility into who has which privileges and how they are used hamstrings security and auditing. And unused and overly-broad privileges can be targeted and exploited, putting the most important keys to your organization’s kingdom in danger.
The good news is these risks can be mitigated quickly. The better news is that the best cloud security solutions won’t handicap your business objectives while doing it.

