


Back to resources
How Claims of an Okta Hack Validate the Need To Separate Authentication and Authorization
March 2022 / 4 min. read /

Understanding the Okta Breach
If there is one thing to come out of the accusation of an Okta hack, it’s the importance of properly managing account privileges.
Keep reading to understand what’s happening, and how bifurcating the authorization and authentication process helps cloud apps and environments stay secure.
In this post:
- What you need to know about the claims of the Okta hack
- How to enforce Defense in Depth by combining strong Authentication and JIT Privilege Authorization
- Watch a Demo below to see how Britive can help
Who's Involved
Hacker group Lapsus$ recently claimed to have breached Okta’s internal environment.
According to Wired, Lapsus$ is responsible for “a string of high-profile victims—including Samsung, Nvidia, and Ubisoft—calamitous leaks, and dramatic accusations that add up to a reckless escalation in an already unlawful industry.”
The article goes on to explain that the hackers have a unique approach to cyber-attacks. Rather than threatening to leak stolen data and encrypted systems, the group focuses on data theft and extortion only. Lapsus$ typically uses phishing attacks to gain valid user credentials to access and steal what data it can without deploying data-encrypting malware.
Okta, an industry-leading identity provider, specializes in user authentication management for thousands of organizations across the globe, including the FCC, Moody’s, and FedEx.
BREAKING: Lapsus$ also claims to have recently breached Microsoft.
What Happened
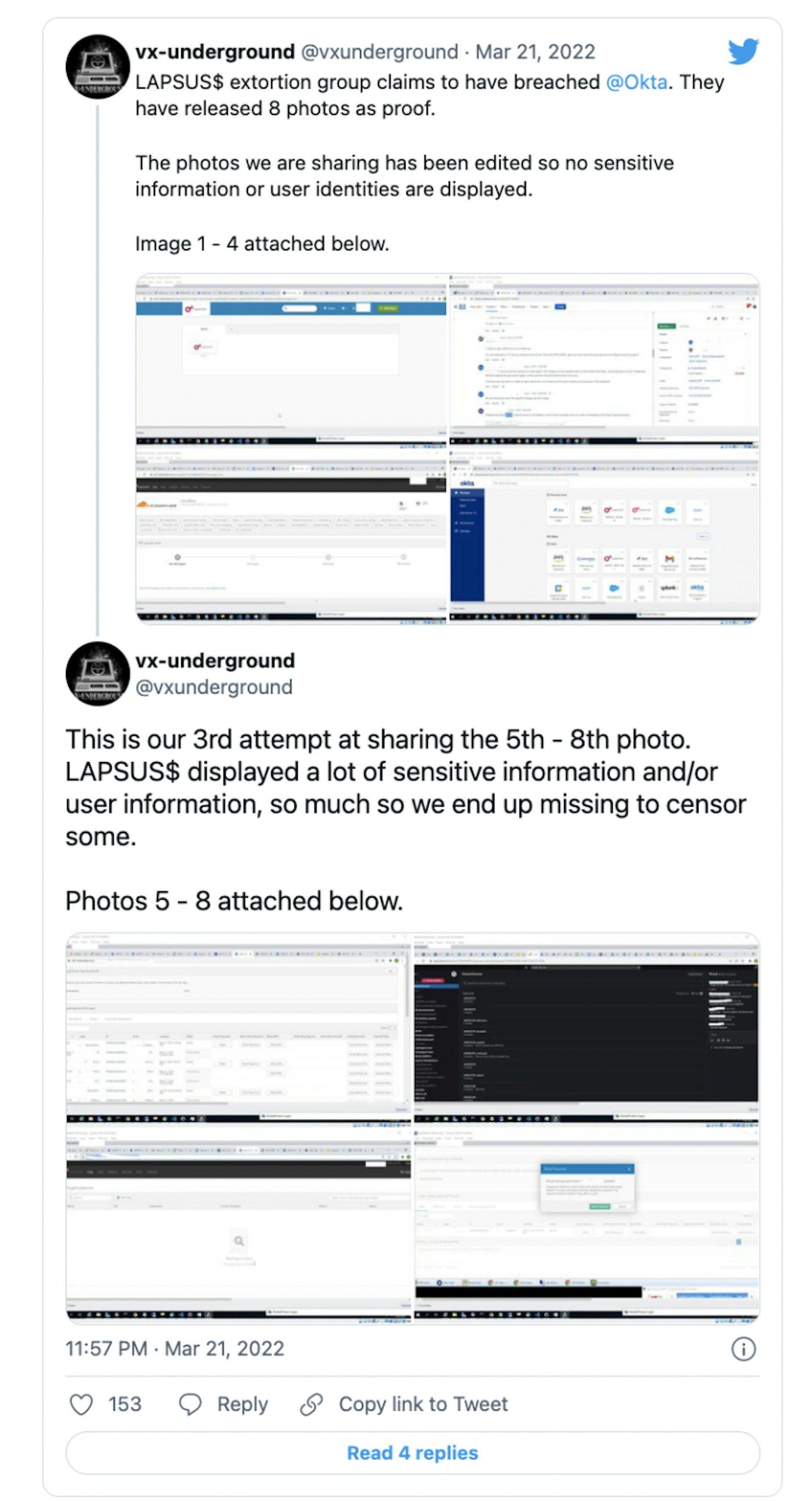
Lapsus$ posted screenshots on Telegram late Monday that claimed to show Okta’s internal systems, including its Slack channels and Cloudflare interface.
Okta spokesperson Chris Hollis told The Verge: “In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor. We believe the screenshots shared online are connected to this January event.”
Hollis suggested there was no evidence of malicious activity beyond the breach that occurred in January, but Lapsus$ claims they have had access now for more than a few months. If the posted screenshots are valid, it would seem to confirm the length of the breach.
The group said the breach’s target was not Okta itself but instead was focused: "ONLY on Okta customers."
Why It Matters
Companies turn to Okta and other identity providers to manage authentication for human users. Using MFA, SSO, and complex password management, Okta provides a necessary layer of authentication security for organizations.
It is important to note that Okta is a premier authentication platform. It is equally important to highlight the defensive advantage companies gain when authentication and authorization are separated.
Because authentication and authorization are often bound together, accounts have standing elevated privileges, which drastically increases an attack surface. In Okta, Super Admins can manage all Okta identities, including corporate admins, 3rd party contractors, and various workloads/tokens.
If a bad actor compromises a Super Admin account, they have full access to the Okta environment, allowing them to:
- Create new users (e.g. Super Admin shadow account)
- Delete logs (i.e. cover up the hack)
- Modify policies Modify access controls
- Turn off security controls
As the alleged hack demonstrates, the ability to stop hackers before they gain admin privileges is critical – both for the IAM vendor and its customers. Therefore, organizations should add an extra layer of security by managing authorization and authentication independent of each other.
How Britive Can Help
The Britive Dynamic Permissioning platform provides an important defensive complement to Okta’s authentication management platform. Britive manages the authorization process separately, giving organizations that critical extra layer of defense.
With Britive, privileges – including Super Admin privileges – are delivered Just-In-Time (JIT). These temporary access privileges fit seamlessly into the approval workflow processes, which empowers users with pre-authorized access privileges that expire automatically after use.
JIT privileges remove the 24/7 risk exposure that results from standing privileges. Moreover, Britive lets you monitor privileged user activity, including when, where and how privileges were invoked and used.
This valuable privileged activity data can also be fed into a SIEM tool to deliver a comprehensive defense in depth approach to all key cloud environments and apps using a unified access model.
Watch the Demo:
Conclusion
The details surrounding the alleged Okta hack are concerning. If true, customers could face serious repercussions. Britive, of course, stands with Okta and hopes for a safe and speedy recovery.
But it is important for the security industry, and customers using security tools, to know that technical innovations exist to help prevent subsequent breaches.
Unlike most cloud security monitoring tools, Britive can effectively mitigate the risk of privilege account compromise (e.g. the Okta Super Admin user) by eliminating standing privileges, while also providing in-depth activity logging and analysis.
If you are serious about protecting access to your cloud environment, contact Britive today.
Our cloud identity experts are standing by.

