


Back to resources
Britive: The First to Climb the Multi-Cloud PAM Maturity Curve
November 2021 / 6 min. read /

Multi-Cloud PAM
Enterprises increasingly rely on more than one cloud service provider (CSP) to accomplish business objectives. Every cloud environment has unique functionality, pricing, and policy models with different integration and support capabilities and constantly evolving features.
Using a multi-cloud environment removes the need to compromise or limit your choices. It also mitigates certain security risks associated with individual cloud environments.
However, because each cloud environment is unique, security challenges multiply and grow in complexity.
Enterprises can struggle to effectively implement privileged access management (PAM) cross-cloud without sacrificing speed and productivity. Absent a cloud-native solution compatible across IaaS, PaaS, SaaS, and DaaS, SecOps and DevOps teams may be unable to cohere and streamline efforts.
The challenge, therefore, is to solve the SecOps and DevOps dilemma – enterprises require better security and better performance cross-cloud. But how?
Cloud Has Disrupted the Security Paradigm
Organizations ringfence on-prem networks via firewalls and traditional security stacks. But user identity is the perimeter to secure in the cloud. Traditional measures cannot protect organizations from sophisticated attacks that attempt to access networks and steal the keys to the kingdom by compromising human and non-human IDs.
Security misconfigurations, overly-privileged user accounts, standing permissions, vulnerable onboarding and offboarding processes – each of these contribute to the increased number of cloud breaches organizations experience annually.
In response to this new security paradigm, numerous solutions are now available to protect and improve the management of privileged cloud users. Such solutions include features like Just-In-Time (JIT) permissions, which grant and revoke privileged user access on the fly, privilege right-sizing, which ensures users receive only the privileges necessary to do their jobs, and improved visibility, which lets organizations monitor and mitigate threats due to user risky behavior.
While these solutions generally advance PAM capabilities on the whole, many cover either IaaS or PaaS or SaaS or DaaS only – instead of all cloud services. Moreover, while certain solutions may cover AWS, Azure, or GCP, they do not cover all major CSPs. And finally, some solutions are not cloud-native, meaning they were designed for on-prem instead of the cloud. We know the cloud, especially multi-cloud, has specific security requirements; “lift and shift” models have proven less than ideal.
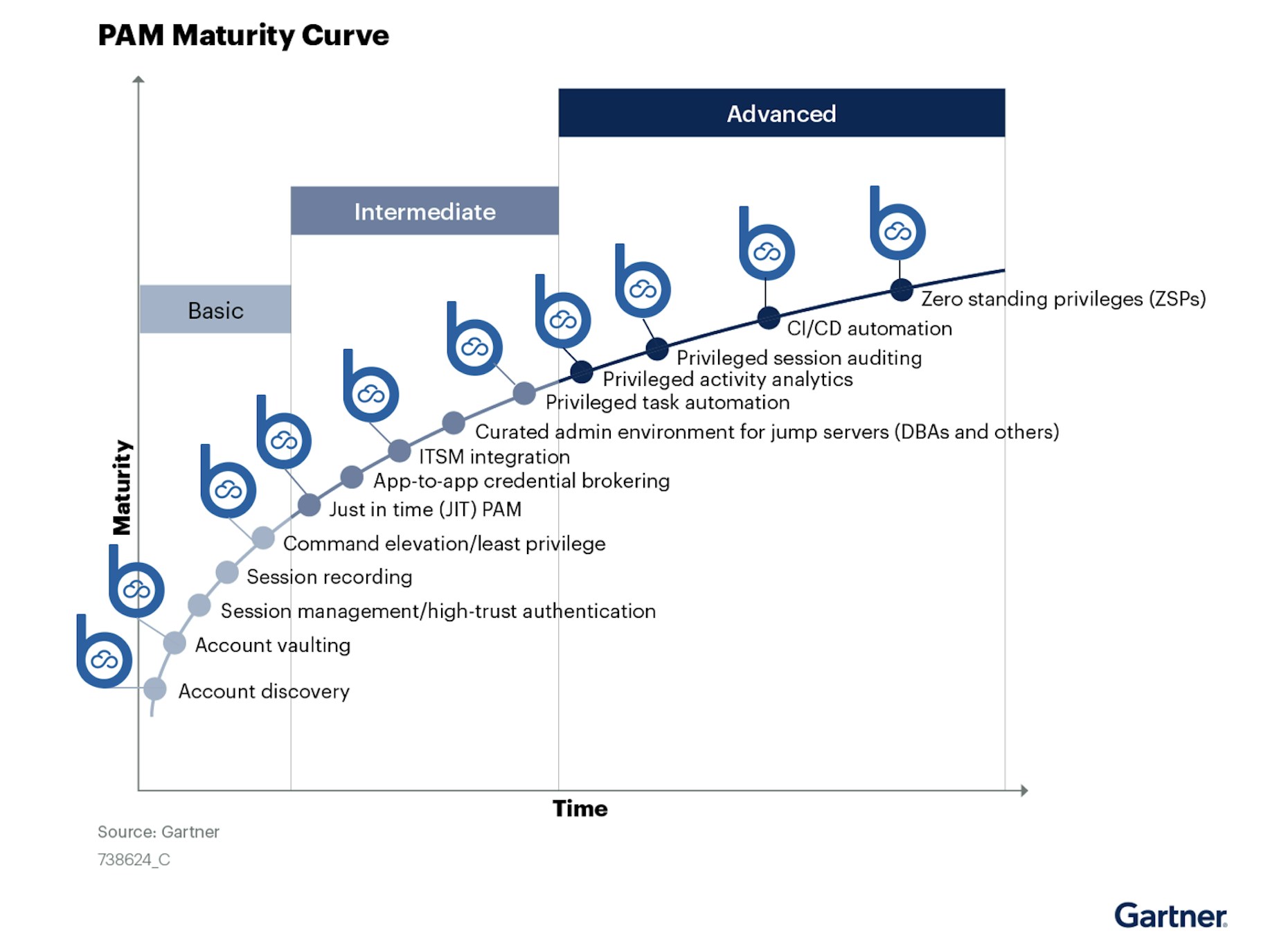
Gartner’s PAM Maturity Curve

In July 2021, Gartner published its PAM maturity curve for security solutions. The curve matures from basic solution features such as account discovery and account vaulting to advanced features such as CI/CD automation and Zero Standing Privileges (ZSP).
The industry’s first, Britive’s multi-cloud privilege management platform features solutions that span the entire curve. Since the platform is cloud-native, it requires no agents or proxies. A unified access model delivers complete visibility cross-cloud, providing essential insight into which permissions users have, and empowers teams with Just-In-Time permissions to grant and revoke permissions on the fly. The platform also integrates with CI/CD automation tools like Jenkins and Terraform so DevOps can build efficiently without security impediments. Of the 14 PAM features Gartner includes, Britive’s platform covers all but 4, and those are on-prem features that do not apply to cloud environments.
Let’s take a closer look at what these features mean for cloud-forward organizations.
Account Discovery: it’s critical to focus on discovery and visibility of cloud account access for both human and machine IDs. The ability to comprehensively identify all accounts with access to applications, databases, containers, and related services is a foundational element of multi-cloud PAM.
Account Vaulting: the cloud has significantly expanded the secrets attack surface and increased pressure to reduce exposure to vulnerabilities. Dynamic permissioning platforms that incorporate account vaulting can overcome these obstacles. When highly-privileged, administrative accounts and passwords are stored in a software vault, the vault controls who is allowed access, when, and for how long.
Command Elevation / Least Privilege: Password-based PAM is no longer enough to secure the cloud. The answer lies in an enterprise cloud infrastructure flexible enough to achieve a continuous state of least privilege access (LPA). With LPA, human and non-human users gain access to restricted resources the moment they need them, only for as long as they need them. This methodology results in the least number of open privileges at any given moment in time.
Just-In-Time (JIT) PAM: With JIT, privileges are granted to users on-demand according to their role, and provide ephemeral access rights that expire automatically – for instance, after a predefined time period, at the close of a timed coding session, or when an employee leaves the organization. This ensures that organizations minimize attack surfaces constantly. When elevated privileges are automatically revoked – all without admin involvement – it adds an essential layer of security to development processes without the overhead that can make certain security solutions unattractive to DevOps teams. As cloud-native entities, these solutions can support highly effective secrets governance initiatives for SMBs and enterprise-level organizations alike.
ITSM Integration: When organizations scale, internal and customer facing IT services can suffer. That’s why it’s essential to align business objectives and user account management processes. Mature, multi-cloud PAM platforms provide a unified access model, which streamlines account management and empowers security teams to efficiently resolve customer issues without sacrificing the speed and flexibility DevOps team need to build effectively.
Privileged Task Automation: Automation can help an organization accomplish repetitive tasks faster, but that leads to users with excessive privileges. If the goal is to reduce your attack surface, it’s important to manage the access users have to various applications and data. Privileged task automation grants only the privileges necessary to complete a given task and nothing more, keeping maintenance and task provisioning under control.
Privileged Activity Analytics: Britive’s Advanced Data Analytics delivers a powerful set of activity monitoring features. These include:
- Privilege right-sizing recommendations
- Risk scoring within AWS accounts
- An access map visualizing access and authorization
- A query engine to flatten access views
- Exportable data via API to external systems
Privileged Session Auditing: Multi-cloud PAM requires comprehensive auditing capabilities. It is only when teams can discover, audit, and control existing access levels and users that organizations can centralize the auditing and policy compliance monitoring process overall.
CI/CD Automation: Recent high-profile attacks have preyed on continuous integration/continuous delivery (CI/CD) systems. That’s why PAM solutions need to harden the delivery pipeline by securing secrets and configuring security controls in CI/CD tools. Seamless integration with automation tools let organizations leverage their existing investments without impeding speed or security.
Zero Standing Privileges: ZSP enforcement mechanisms empower cloud infrastructure, DevOps, IT, and security teams with dynamic and intelligent privileged access administration. These solutions work on the concept of zero trust, which means no one and no thing is trusted with permanent standing access to your cloud accounts and data. Access is temporary and strictly controlled. Dynamically adding and removing privileges enables DevSecOps to maintain a ZSP security posture.
Conclusion
The Britive multi-cloud privilege management platform solves the SecOps and DevOps dilemma by delivering better security and cross-cloud performance. As a result, enterprises can achieve least privilege access and zero standing permissions across all key CSPs while moving toward an enforced policy of ZSP.
A mature multi-cloud PAM solution liberates enterprises from the inherent costs, functionality limitations, and security challenges of cloud platform silos. It accelerates time-to-value and bolsters ROI. And because Britive uses cloud-native APIs, even large enterprises can be up and running in less than 15 minutes.
For a custom demo, book a demo and see the Britive platform in action.

